

ERMProtect
ERMProtect identify IT vulnerabilities, secure systems, and train employees to recognize when they are being targeted by hackers. Visit us :
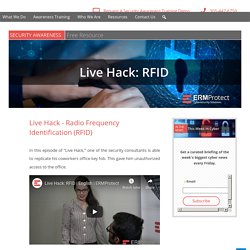
Live Hack: Radio Frequency Identification (RFID) Cyber Tip of the Day – Trojans To help promote Cybersecurity Awareness, we would like to start your week with a tip to stay safe online.
Today’s subject: Trojans. Spot the Phish: Government Websites. Cyber Tip of the Day – Trojans To help promote Cybersecurity Awareness, we would like to start your week with a tip to stay safe online.
Today’s subject: Trojans. Trojans are a type of malware that pretend to be trustworthy, while they … Live Hack: Swift Trojan. What To Do If You Have Just Experienced A Data Breach? According to the well-known antivirus company Malwarebytes, 2018 was the year of the data breach.
Many great companies were hacked; great tech companies, retailers, and hospitality providers, and that is only the data captured by the Malwarebytes. It is hard to know what a data breach is, and what to do. On many occasions, the company does not know they have been hacked until years later, making this a big issue for the security of the company. By the time any company is able to target the issue and find the right technician to fix it, the damage is already done. Not only will they have caused a problem inside your digital footprint, but they now have access to any information they may have gotten from the breach. Two years have passed from 2018, companies have improved their online security, many online breaches have allowed spyware software to understand the issue, and tackle it better. What Is Digital Forensics & How Can It Benefit You? It seems that there’s something threatening you wherever you go these days.

Schools and other public locations have been the target of acts of horrendous violence and there’s a lot of division amongst people with opposing views which has led to tragic results. This same concern for safety has now transitioned to the digital realm in the past few years as malware and cyber attacks have become rampant, even targeting the mainframes of political and higher education institutions. As a result, corporations and other establishments have turned to the best cybersecurity services available to maximize their mainframe’s security. The focus of this article will be on digital forensics companies and the services they and other security awareness training vendors offer their clients, and how all of this can benefit you. Qualities Of An Excellent Penetration Testing Firm. Interested in learning about the benefits of a penetration testing firm?
We’ve got you covered. PCI Service Companies ensure that the security of a company’s IT infrastructure isn’t compromised. They run a series of tests as a means of checking and ensuring everything is up and running smoothly. An Introduction To White Hat Hack & Why You Should Consider It. People used to be afraid of burglars breaking into their homes and stealing their valuables.

Even though home security has taken extensive leaps in its effectiveness, this same fear is alive and well in the age of the internet. One of the biggest threats that people face in today’s age is that of malware and cybercrime. Live Hack: Hand in the Cookie Jar - Cybersecurity and Training. Cyber Tip of the Day - Anti-Virus - Cybersecurity and Training. How to Revamp your Security Awareness Training. Which of these Career Opportunity Emails are Phishing Attempts? Are these Payments Websites Real or Phony? Which of these Insurance Emails are Phishing Attempts? ERMProtect Launches Stingray, An Automated, Simulated Phishing Tool.
October 8, 2019 (Miami, FL) - ERMProtect, a leading cybersecurity firm, today launched Stingray, an easy-to-use, fully automated phishing simulation tool that helps organizations harden their defenses against phishing attacks.

ERMProtect Expands Privacy Practice as Data Protection Concerns Rise. August 19, 2019 MIAMI, FL – ERMProtect, a leading cybersecurity firm, is pleased to announce the expansion of its Privacy Practice to help clients comply with an ever-changing regulatory landscape.

The Privacy group will focus on developing, implementing and reviewing data protection practices at client organizations to ensure compliance, enhance brand reputation, elevate customer trust and boost profits. Spoke at the 3rd Annual GRC Conference on June 21, 2019. Our Director of Information Security & Privacy Consulting will be speaking at the 3rd Annual GRC Conference on June 21, 2019.

Dr. Rey Leclerc Sveinsson will be speaking on the GDPR vs. CCPA, the Similarities & Differences. The GRC Conference is the premier summer conference for South Florida IT executives in the private and public sectors and provides opportunities for IT leaders (CIOs, CISOs, CSOs, CTOs, and IT Directors) and other industry practitioners to share their experiences and network while hearing informative and engaging presentations. Topics will cover pertinent areas in the security world including security automation, security responsibilities for cloud services, incident response, IoT and mobile devices security. Where: 901 NW 35th St. How To Protect Yourself From The Dangers Of Data Hacking. In today's day and age, much of our lives are conducted on the internet, whether you are making a doctor's appointment or paying your rent; it's probably being accomplished via the internet.
This is great, the internet has single-handedly connected all the four corners of the world with the click of a mouse or press of a key. People can now see what's going on across the world from the comfort of their own bed. While the internet has brought new heights to our society, it also introduced negative aspects that no one could have foreseen. ERMProtect Named a Gartner “Vendor to Note” for Security Awareness Training Product. MIAMI--ERMProtect, a leading cybersecurity & training company, has been named by Gartner as a “vendor to note” in its latest Magic Quadrant for Security Awareness Computer-Based Training.
Gartner, the world’s foremost IT research and advisory firm, recognized ERMProtect in its July 2019 report. This is the second time that Gartner has listed ERMProtect in this vendor category. How To Create Better Data Security. 2017 marked the year that data surpassed oil in value, making it the most valuable resource in the world. This makes data breaching a growing threat in today’s online world, especially for businesses and their business that is conducted primarily online. Everyone leaves a digital trail when purchasing clothes, paying bills, going to the doctor, etc. If others get a hold of where you’ve been, what you buy, and what you want they can use it in a million different ways without your consent. If you own a business that’s run via the internet, the risks become even higher.
Benefits Of Doing The Cyber Security Training Online. Jennifer Roberts Connect Menu Jennifer Roberts Added on 27 August. Things You Must Know About A Security Awareness Company. Cybersecurity is an issue of great concern in today’s digital age. In recent years, the number of cyber attacks and malware infestations have drastically increased. Which of these Emails are Phishes? Spot e-Commerce Phishing Email. Can You Spot the Real Amazon Email? Can You Spot the Real Costco Email? ERMProtect Named a Gartner “Vendor to Note” for Security Awareness Training Product. ERMProtect Expands Privacy Practice as Data Protection Concerns Rise. ERMProtect Named a Gartner “Vendor to Note” for Security Awareness Training Product. ERMProtect Cybsecurity Solutions Certified As PCI Forensic Investigator By Payment Card Industry. MIAMI, FL - (April 24, 2019) ERMProtect, a leading cybersecurity firm, today announced it has been certified as a PCI Forensic Investigator (“PFI”) by the Payment Card Industry Security Standards Council.
Live Hack: Spoofed! Live Hack: Malvertising. Use These Proven Tactics To Keep Yourself Safe From A Cyberattack. Why Companies like Amazon and Apple are Paying Hackers to Break into Their Sites. The Hidden Reason Behind White Hat Testing. ERMProtect Adds Digital Games to Cyber Security Awareness Training Platform. How Cloud Compliance Standards Will Change In The Future. 6 Tips To Improve IT Security Awareness At Your Company.
The Common Questions About Understanding SOC Assessments. Best Cybersecurity Expert Joins ERMProtect to Help Lead Information Security. Cybersecurity Expert Joins ERMProtect to Help Lead Information Security & Privacy Practice. Best Cybersecurity Expert Joins ERMProtect to Help Lead Information Security. Basics Of The Window Phone For Digital Forensics. ERMProtect security risk management consultants Coral Gables, FL 33134 Connect. Top 10 Elements Of Cyber Security Awareness Training Programs. There used to be a time when people stored their valuables and financial documentation in safes within their house or if you were wealthy, they would store these items at the bank in safe boxes.
But now, in the digitalization of our society, it is far easier to store things online, but some industries have become quite vulnerable to cyber attacks. Spot the Phish: Apple. ERMProtect Adds Digital Games to Cyber Security Awareness Training Platform. ERMProtect Cybersecurity Solutions Launches New Security Awareness Training Content - Cybersecurity and Training. Why Your Corporation Needs a Security Risk Consultant. Cyber Security Awareness: Training, Threats and Preventive Measures. Protective Security Training - ERMProtect. Would You Connect To The Evil Twin? - Cybersecurity and Training. ERMProtect Launches Free "Live Hack" Video Series To Educate Public About Cyber Safety - Cybersecurity and Training.
Tips to Securing Your Social Media. Everyday millions log into their favorite social media platforms to view, show and learn about their favorite celebrities and their lives, update people on their personal lives or see what their friends are up to. Businesses have taken part on social media, allowing fans and competitors to keep up with their everyday workings. Social Media has done an amazing job connecting people and sharing information between these individuals. However, as with most concepts, there are some negative issues surrounding social media. Hacked profiles and stolen identities continue to be prevalent issues. Images can be used in some of the craziest places on the web, often without the individuals knowledge or consent. Strong Password During the application of your social media account, in order to create your profile, you are asked to create a password. Another aspect to consider would be the inclusion of numbers and symbols in your password.
Do Not Save Passwords. 5 Things You Need to Do Following the Marriott and Quora Data Breaches. Cyber Attacks Continue to Rise - Cybersecurity and Training. Millions of Chinese CVs Exposed Online - Cybersecurity and Training. Cyber Criminals Attack SEC - Cybersecurity and Training.