

Telvent keeps detailed blueprints on more than half of all the oil and gas pipelines in North and South America, and has access to their systems.
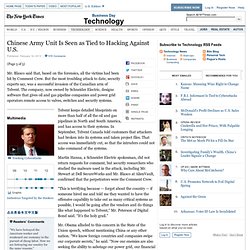
In September, Telvent Canada told customers that attackers had broken into its systems and taken project files. That access was immediately cut, so that the intruders could not take command of the systems. Martin Hanna, a Schneider Electric spokesman, did not return requests for comment, but security researchers who studied the malware used in the attack, including Mr. Stewart at Dell SecureWorks and Mr. Blasco at AlienVault, confirmed that the perpetrators were the Comment Crew. “This is terrifying because — forget about the country — if someone hired me and told me they wanted to have the offensive capability to take out as many critical systems as possible, I would be going after the vendors and do things like what happened to Telvent,“ Mr. Mr. Mr. “Right now there is no incentive for the Chinese to stop doing this,” said Mr. Carlos Barria/Reuters The headquarters of Unit 61398, center, in Shanghai. The unit of the People’s Liberation Army is believed to have resumed its attacks on American companies and government agencies.
The Obama administration had bet that “naming and shaming” the groups, first in industry reports and then in the Pentagon’s own detailed survey of Chinese military capabilities, might prompt China’s new leadership to crack down on the military’s highly organized team of hackers — or at least urge them to become more subtle. But Unit 61398, whose well-guarded 12-story white headquarters on the edges of Shanghai became the symbol of Chinese cyberpower, is back in business, according to American officials and security companies. It is not clear precisely who has been affected by the latest attacks. According to security experts, the cyberunit was responsible for a 2009 attack on the Coca-Cola Company that coincided with its failed attempt to acquire the China Huiyuan Juice Group.
This 12-story building on the outskirts of Shanghai is the headquarters of Unit 61398 of the People’s Liberation Army.
China’s defense ministry has denied that it is responsible for initiating digital attacks. The building off Datong Road, surrounded by restaurants, massage parlors and a wine importer, is the headquarters of P.L.A. Unit 61398. Hasan Sarbakhshian/Associated Press Iran’s nuclear enrichment facility at Natanz.
Mr. Stuxnet is a computer worm[1] that was discovered in June 2010.
It was designed to attack industrial programmable logic controllers (PLCs). PLCs allow the automation of electromechanical processes such as those used to control machinery on factory assembly lines, amusement rides, or centrifuges for separating nuclear material. Exploiting four zero-day flaws,[2] Stuxnet functions by targeting machines using the Microsoft Windows operating system and networks, then seeking out Siemens Step7 software. Stuxnet reportedly compromised Iranian PLCs, collecting information on industrial systems and causing the fast-spinning centrifuges to tear themselves apart.[3] Stuxnet’s design and architecture are not domain-specific and it could be tailored as a platform for attacking modern SCADA and PLC systems (e.g. in the automobile or power plants), the majority of which reside in Europe, Japan and the US.[4] Stuxnet reportedly ruined almost one-fifth of Iran's nuclear centrifuges.[5] Discovery[edit]
Yes, yes, we know that China has a lot of fake handbags, knockoff watches, and pirated DVDs.
That's ho-hum, but the country seems to be all about pushing the envelope and testing the limits of what can be faked. Let's take a look at the 9 most outrageous things ever faked in China. 1. Fake Receipts Photo: China's Ministry of Public Security. The American officials would not say which countries in the Persian Gulf have signed up for help in countering Iran’s computer abilities.
But the list, some officials say, includes the nations that have been the most active in tracking Iranian arms shipments, intercepting them in ports and providing intelligence to the United States about Iranian actions. The three most active in that arena are Saudi Arabia, the United Arab Emirates and Bahrain. In Asia, the countries most worried about being struck by North Korean computer attacks are South Korea and Japan. Barack Obama has ordered his senior national security and intelligence officials to draw up a list of potential overseas targets for US cyber-attacks, a top secret presidential directive obtained by the Guardian reveals.
The 18-page Presidential Policy Directive 20, issued in October last year but never published, states that what it calls Offensive Cyber Effects Operations (OCEO) "can offer unique and unconventional capabilities to advance US national objectives around the world with little or no warning to the adversary or target and with potential effects ranging from subtle to severely damaging". It says the government will "identify potential targets of national importance where OCEO can offer a favorable balance of effectiveness and risk as compared with other instruments of national power".