

BYOD is not for every company, or every employee. Posted on 28 August 2012.
The rise of bring your own device (BYOD) programs is the single most radical shift in the economics of client computing for business since PCs invaded the workplace, according to Gartner. Safeguard Facebook photos with McAfee Social Protection. Posted on 28 August 2012.

McAfee announced the availability of a free public beta of McAfee Social Protection, a new app for Facebook that protects users’ photos from being shared without their permission. Offered as a Facebook app together with a browser plug-in, McAfee Social Protection lets users select which friends have access to their photos and makes pictures appear blurry to everyone else.
For selected friends, the photos will be displayed properly once those friends have installed the app, creating a second layer of protection. McAfee Social Protection gives users a safe platform to share photos without having to worry about them going viral or being uploaded onto the Internet by someone else. Cyberattacks Carried Out Against Forces In Afghanistan, U.S. General Says. Unpatched Java vulnerability exploited in targeted attacks, researchers say. Attackers are exploiting a new and unpatched vulnerability that affects the latest version of Java -- Java 7 Update 6 -- in order to infect computers with malware, according to researchers from security vendor FireEye.
So far, the vulnerability has been exploited in limited targeted attacks, FireEye's senior staff scientist Atif Mushtaq said Sunday in a blog post. "Most of the recent Java run-time environments i.e., JRE 1.7x are vulnerable. " The exploit is hosted on a website that resolves to an Internet Protocol address in China and its payload is a piece of malware that connects to a command and control server located in Singapore. Singapore suffers from 'false sense of security' Singapore's "vibrant" IT security environment, low rate of reported breaches and incidents, and not being at the frontlines of online attacks have lulled local businesses into a "false sense of security" which leaves them vulnerable.
According to Ngair Teow Hin, founder and CEO of security firm SecureAge, the "vibrant" security scene in the city-state with more than 100 security companies here, and existing laws such as the Computer Misuse Act, help deter people from hacking into organizations here. Blue Coat takes malware hunt to the node.
In the war on malware, it is important not only to recognize the malicious software, but also where it is coming from.
Blue Coat, a web security firm, said that tracking "malnets" through geolocation of their infrastructure nodes is helping it respond more quickly and effectively to attacks that number in the millions every day. On its website the company provides a graph of the number of daily threats over the previous week. The number of blocked threats reported for Aug. 26 -- a bit lower than the previous six days -- was 17,765,686. Map of state data breach notification laws. Posted on 28 August 2012.
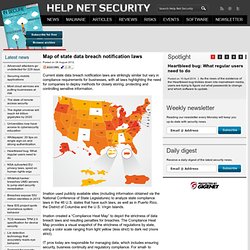
Current state data breach notification laws are strikingly similar but vary in compliance requirements for businesses, with all laws highlighting the need for companies to deploy methods for closely storing, protecting and controlling sensitive information. Imation used publicly available sites (including information obtained via the National Conference of State Legislatures) to analyze state compliance laws in the 46 U.S. states that have such laws, as well as in Puerto Rico, the District of Columbia and the U.S. Trend Micro Deep Security 9 released. Posted on 28 August 2012.

Trend Micro announced Deep Security 9, a server security platform designed to provide server, application and data security across physical, virtual and cloud environments Deep Security leverages both agentless and agent-based protection mechanisms to automatically and efficiently secure virtual servers and desktops, and private and public clouds and accelerate ROI. Don't let the UN steal the Internet. Fake Facebook photo notifications carry malware. Quantum processor's prime feat raises security issues. Researchers in California have designed and built a quantum processor capable of factoring 15 into its primes — with major implications for computer security.
Quantum computing is famous for its potential to obliterate current cryptographic techniques. Much of cryptography today relies on the lack of processing power in classical computers to factor a very large number into its primes. Splunk delivers operational intelligence for the cloud. Posted on 28 August 2012.

Splunk announced Splunk Storm, a cloud service based on the Splunk software and is for organizations that develop and run applications in the public cloud, using services such as Amazon Web Services (AWS), Heroku, Google App Engine, Rackspace, and others. With Splunk Storm, users can diagnose and troubleshoot application problems, gain visibility and insight into cloud-based applications, and monitor business metrics for operational intelligence. "As more organizations and developers move their projects to the cloud, we want to be there with them," said Godfrey Sullivan, Chairman and CEO, Splunk. "Customers run Splunk Enterprise on premises and in clouds today, and now, Splunk Storm provides developers with an easy-to-use, subscription version of our software.
Feedback during the public beta program has been extremely positive, with hundreds of active projects during the beta phase. " Key features: ID Don't Mean a Thing Unless Its Got that Integration Thing. Hackers allegedly breached Saudi Aramco again. Posted on 28 August 2012.
Saudi Aramco, the national oil company of Saudi Arabia and the biggest oil company in the world, has issued a statement announcing that it has restored all its main internal network services that were impacted in a recent cyber attack which affected about 30,000 workstations - a number that corresponds with that shared by the Cutting Sword of Justice, the hacker group that took credit for the breach. The company's primary enterprise systems of hydrocarbon exploration and production were unaffected as they operate on isolated network systems, the statement confirmed. The production plants were also fully operational. Digital Dao: Who's Responsible for the Saudi Aramco Network Attack?