

Security. Denial-of-service attack. DDoS Stacheldraht Attack diagram.
Perpetrators of DoS attacks typically target sites or services hosted on high-profile web servers such as banks, credit card payment gateways, and even root nameservers. DoS threats are also common in business,[1] and are sometimes responsible for website attacks.[2] This technique has now seen extensive use in certain games, used by server owners, or disgruntled competitors on games, such as server owners' popular Minecraft servers. Ping flood. A flood ping can also be used as a diagnostic for network packet loss and throughput issues.[1] References[edit] Jump up ^ See also[edit] External links[edit]
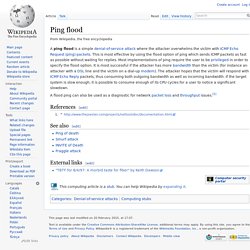
SYN flood. A normal connection between a user (Alice) and a server.
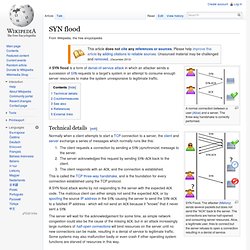
The three-way handshake is correctly performed. SYN Flood. The attacker (Mallory) sends several packets but does not send the "ACK" back to the server. The connections are hence half-opened and consuming server resources. UDP flood attack. Check for the application listening at that port;See that no application listens at that port;Reply with an ICMP Destination Unreachable packet.
Thus, for a large number of UDP packets, the victimized system will be forced into sending many ICMP packets, eventually leading it to be unreachable by other clients. The attacker(s) may also spoof the IP address of the UDP packets, ensuring that the excessive ICMP return packets do not reach them, and anonymizing their network location(s). Most operating systems mitigate this part of the attack by limiting the rate at which ICMP responses are sent. Smurf attack. The Smurf Attack is a distributed denial-of-service attack in which large numbers of Internet Control Message Protocol (ICMP) packets with the intended victim's spoofed source IP are broadcast to a computer network using an IP Broadcast address.
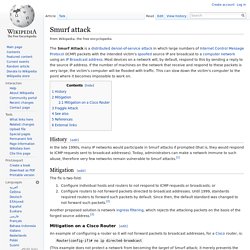
Most devices on a network will, by default, respond to this by sending a reply to the source IP address. If the number of machines on the network that receive and respond to these packets is very large, the victim's computer will be flooded with traffic. This can slow down the victim's computer to the point where it becomes impossible to work on. History[edit] In the late 1990s, many IP networks would participate in Smurf attacks if prompted (that is, they would respond to ICMP requests sent to broadcast addresses).
Anonymous (group) Low Orbit Ion Cannon. LOIC. mIRC: Internet Relay Chat client. Internet Relay Chat. Internet Relay Chat (IRC) is an application layer protocol that facilitates transfer of messages in the form of text.
The chat process works on a client/server model of networking. IRC clients are computer programs that a user can install on their system. Heartbleed. Logo representing the Heartbleed bug, created by Finland's Codenomicon company.
The logo and the name "Heartbleed", which also originates from the company, have contributed to public awareness of the issue.[1][2] Heartbleed is a software bug in the open-source cryptography library OpenSSL. At its public disclosure, on April 7, 2014, some 17 percent (around half a million) of the Internet's secure web servers certified by trusted authorities were believed to have been vulnerable to the attack, allowing theft of the servers' private keys and users' session cookies and passwords.[3][4][5][6][7] The issue is registered in the Common Vulnerabilities and Exposures system as CVE-2014-0160.[8] History[edit] The Heartbeat Extension for the Transport Layer Security (TLS) and Datagram Transport Layer Security (DTLS) protocols is a proposed standard specified by RFC 6520, published in February 2012. Heartbleed Explanation.
Shellshock (software bug) "Bash bug" redirects here.
Stuxnet. Stuxnet is a computer worm[1] that was discovered in June 2010.
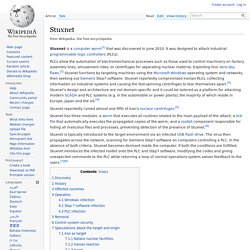
It was designed to attack industrial programmable logic controllers (PLCs). PLCs allow the automation of electromechanical processes such as those used to control machinery on factory assembly lines, amusement rides, or centrifuges for separating nuclear material. Exploiting four zero-day flaws,[2] Stuxnet functions by targeting machines using the Microsoft Windows operating system and networks, then seeking out Siemens Step7 software.
Piggybacking (security) In security, piggybacking refers to when a person tags along with another person who is authorized to gain entry into a restricted area, or pass a certain checkpoint.[1] The act may be legal or illegal, authorized or unauthorized, depending on the circumstances.
However, the term more often has the connotation of being an illegal or unauthorized act. To describe the act of an unauthorized person who follows someone to a restricted area without the consent of the authorized person, the term tailgating is also used. "Tailgating" implies without consent (similar to a car tailgating another vehicle on the freeway), while "piggybacking" usually implies consent of the authorized person. Piggybacking came to the public's attention particularly in 1999, when a series of weaknesses were exposed in airport security. Piggybackers have various methods of breaching security. Shoulder surfing (computer security) In computer security, shoulder surfing refers to using direct observation techniques, such as looking over someone's shoulder, to get information.[1] It is commonly used to obtain passwords, PINs, security codes, and similar data.
How do I recover from Hosts file hijacking? Security. If you are unable to access some Internet sites, or requests to one Internet site are redirected elsewhere, but you can access other Internet sites, your problem may be "Hosts File Hijacking. " What the Hosts file is: On the Internet, people usually talk about Internet sites using domain names, like microsoft.com, dshield.org, whitehouse.gov or gc.ca, ut computer networks function using IP addresses. Data to be sent on the Internet is broken up into chunks called packets (also called datagrams or "messages"). SQL injection. A classification of SQL injection attacking vector as of 2010. SQL injection attacks allow attackers to spoof identity, tamper with existing data, cause repudiation issues such as voiding transactions or changing balances, allow the complete disclosure of all data on the system, destroy the data or make it otherwise unavailable, and become administrators of the database server.
In a 2012 study, it was observed that the average web application received 4 attack campaigns per month, and retailers received twice as many attacks as other industries.[2] History[edit] The first public discussions of SQL injection started appearing around 1998;[3] for example, a 1998 article in Phrack Magazine.[4] Form[edit] Exploits of a Mom. DNS spoofing. Overview of the Domain Name System[edit] IP address spoofing. MAC spoofing. ARP spoofing. Cross-site scripting. Background[edit] Privilege escalation. Buffer overflow. Technical description[edit] How Cybercrime Exploits Digital Certificates. What is a digital certificate? The digital certificate is a critical component of a public key infrastructure. Serious Security: Google finds fake but trusted SSL certificates for its domains, made in France. Google announced over the weekend that it recently came across a bunch of fake SSL certificates for some of its own domains.
DigiNotar. DigiNotar was a Dutch certificate authority owned by VASCO Data Security International.[1] On September 3, 2011, after it had become clear that a security breach had resulted in the fraudulent issuing of certificates, the Dutch government took over operational management of DigiNotar's systems.[2] That same month, the company was declared bankrupt.[3] Side channel attack. Why are we still vulnerable to side-channel attacks? (and why should I care?) How the NSA cheated cryptography. File Slack Vs RAM Slack Vs Drive Slack - Checkmate.
Hiding Data, Forensics and Anti-Forensics. Cold boot attack. DMA attack.