

Radio access network. A radio access network (RAN) is part of a mobile telecommunication system.
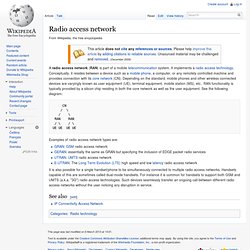
It implements a radio access technology. Conceptually, it resides between a device such as a mobile phone, a computer, or any remotely controlled machine and provides connection with its core network (CN). Depending on the standard, mobile phones and other wireless connected devices are varyingly known as user equipment (UE), terminal equipment, mobile station (MS), etc.. RAN functionality is typically provided by a silicon chip residing in both the core network as well as the user equipment. See the following diagram: Examples of radio access network types are: It is also possible for a single handset/phone to be simultaneously connected to multiple radio access networks. Storage area network. A SAN does not provide file abstraction, only block-level operations.
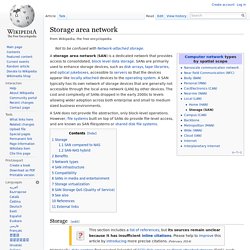
However, file systems built on top of SANs do provide file-level access, and are known as SAN filesystems or shared disk file systems. Storage[edit] Historically, data centers first created "islands" of SCSI disk arrays as direct-attached storage (DAS), each dedicated to an application, and visible as a number of "virtual hard drives" (i.e. LUNs).[1] Essentially, a SAN consolidates such storage islands together using a high-speed network. Operating systems maintain their own file systems on their own dedicated, non-shared LUNs, as though they were local to themselves. Despite such issues, SANs help to increase storage capacity utilization, since multiple servers consolidate their private storage space onto the disk arrays.
Common uses of a SAN include provision of transactionally accessed data that require high-speed block-level access to the hard drives such as email servers, databases, and high usage file servers. 5. Network-attached storage. Network-attached storage (NAS) is file-level computer data storage connected to a computer network providing data access to a heterogeneous group of clients.
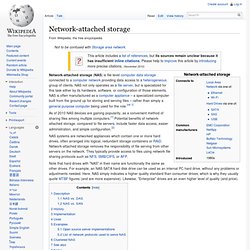
NAS not only operates as a file server, but is specialized for this task either by its hardware, software, or configuration of those elements. NAS is often manufactured as a computer appliance – a specialized computer built from the ground up for storing and serving files – rather than simply a general purpose computer being used for the role. [nb 1] As of 2010[update] NAS devices are gaining popularity, as a convenient method of sharing files among multiple computers.[1] Potential benefits of network-attached storage, compared to file servers, include faster data access, easier administration, and simple configuration.[2] Note that hard drives with "NAS" in their name are functionally the same as other drives.
IPsec. IPsec is an end-to-end security scheme operating in the Internet Layer of the Internet Protocol Suite, while some other Internet security systems in widespread use, such as Transport Layer Security (TLS) and Secure Shell (SSH), operate in the upper layers of the TCP/IP model.
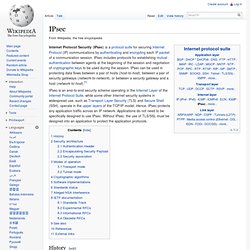
Hence, IPsec protects any application traffic across an IP network. Applications do not need to be specifically designed to use IPsec. Without IPsec, the use of TLS/SSL must be designed into an application to protect the application protocols. History[edit] The IPsec working group in the IETF was started to create an open freely available and vetted version of protocols that had been developed under NSA contract in the Secure Data Network System (SDNS) project. In July 1994, Wei Xu at Trusted Information Systems continued this research which was completed successfully on the BSDI platform after a few months. Security architecture[edit] [edit] AH operates directly on top of IP, using IP protocol number 51.[15]
IPsec. User Datagram Protocol. Un article de Wikipédia, l'encyclopédie libre.
Pour les articles homonymes, voir UDP. Le User Datagram Protocol (UDP, en français protocole de datagramme utilisateur) est un des principaux protocoles de télécommunication utilisés par Internet. Il fait partie de la couche transport de la pile de protocole TCP/IP : dans l'adaptation approximative de cette dernière au modèle OSI, il appartiendrait à la couche 4, comme TCP. Il est détaillé dans la RFC 768. Le rôle de ce protocole est de permettre la transmission de données de manière très simple entre deux entités, chacune étant définie par une adresse IP et un numéro de port. L'intégrité des données est assurée par une somme de contrôle sur l'en-tête. La nature de UDP le rend utile pour transmettre rapidement de petites quantités de données, depuis un serveur vers de nombreux clients ou bien dans des cas où la perte d'un datagramme est moins gênante que l'attente de sa retransmission.
Le paquet UDP est encapsulé dans un paquet IP. Longueur.