

Libpcap packet capture tutorial. This section will focus on peaking into the packets to extract the information (which is what we wanted to begin with).

First off we must arm ourselves! Go ahead and get all the relevent RFC's. Lets start off with RFC 791 (IP) RFC 768 (UDP) RFC 826 (ARP) RFC 792 (ICMPv4) and of course RFC 793 (TCPv4) The truth is, once you have these files you dont really need me *sigh* but then again... why right your own code when you can just copy mine! Hehe I would highly recommend you use another packet sniffer to double check your programs... tcpdump will do just fine, and ethereal just kicks ass, you can get either (and more!!) I would prefer not to have to rewrite the main body of the program for each new example like I have done previously. I will be using the above program and merely replacing the callback function my_callback for demo programs in this section. Lets start by looking at the datalink headers. Streams - Play with pcap files. Streams is a tool for browsing, mining and processing TCP streams in pcap files.
It provides a command line prompt for filtering, selecting and dumping reassembled session data. Security Analytics: having fun with Splunk and a packet capture file. It’s been quite a long time since my last post here.
I’m now taking the opportunity to share one article I wrote about Splunk , which might be of some help to the community. Since I’ve been using that technology for a while, I’ve decided to leverage such knowledge in order to renew one GIAC certification I got in the past (GCIA). Basically, the paper’s content is about installing Splunk Enterprise (freely available version) on a Linux machine, getting network data processed based on tshark’s output, and finally extracting some interesting stats and charts out of it.
It was also a fun way to introduce Splunk’s data mining features, which might hopefully enable users to develop new ideas based on the approach presented in there. As expected, there should be many other ways to accomplish the same results while processing IP packet headers, whether it’s using Splunk or not, so I would really appreciate receiving feedback about other approaches used out there. Like this: Android pcap viewer and converter trend: Advanced Image Viewer and Converter, Picture Viewer and Converter Suite, Viewer PPT Converter. Duplicate Packet Filtering. Let’s take a quick moment to work through the steps of cleaning out a trace file that contains duplicate packets.
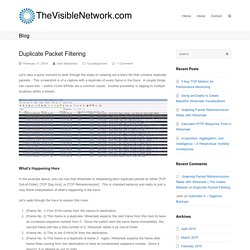
This screenshot is of a capture with a duplicate of every frame in the trace. A couple things can cause this – switch VLAN SPANs are a common cause. Another possibility is tapping in multiple locations within a stream. Quick and dirty packet capture data extraction - PacketLife.net. If you ever find yourself needing to reconstruct binary data contained within a packet capture, there is a simple way to do so on the fly using only Wireshark and a utility called foremost.
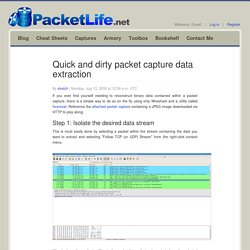
Reference the attached packet capture containing a JPEG image downloaded via HTTP to play along. Step 1: Isolate the desired data stream This is most easily done by selecting a packet within the stream containing the data you want to extract and selecting "Follow TCP (or UDP) Stream" from the right-click context menu. Wireshark applies a display filter to the packet list so that only packets from the selected stream are shown, and it invokes the stream content window shown below.
Network Packet Forensics System & Training and Technology. Artem Dinaburg's Blog: Bitsquatting PCAP Analysis Part 1: Analyzing PCAPs using Unix command line tools. This blog post was originally going to be about domain name distribution in the bitsquatting PCAPs, but I found a problem with my first analysis.
The problem has been turned into an opportunity, and now this blog post is about domain name distribution in the bitsquatting PCAPs, and a tutorial on how to determine the distribution yourself! This blog post/tutorial will follow the process I used to answer the following questions: How many unique domains appear in queries directed at the bitsquatting nameserver? Answer: 4271.What is the frequency distribution of queried domains? NetFort Tips & Tricks - Using LANGuardian to analyze PCAP files. Did you know that NetFort LANGuardian can analyze PCAP files created by network analyzers such as tcpdump, Wireshark and Microsoft Network Monitor?
Every LANGuardian system includes a PCAP sensor. To analyze PCAP data, simply upload your file and associate it with the sensor. LANGuardian will add the contents of the PCAP file to your traffic database, allowing you to analyze the data in the same way you analyze data captured by LANGuardian itself. Pcap. Parsing pcap files with dpkt (Python) - codeitive.com. I'm trying to parse a previously-captured trace for HTTP headers using the dpkt module: import dpkt import sys f=file(sys.argv[1],"rb") pcap=dpkt.pcap.Reader(f) for ts, buf in pcap: eth=dpkt.ethernet.Ethernet(buf) ip=eth.data tcp=ip.data if tcp.dport==80 and len(tcp.data)>0: try: http=dpkt.http.Request(tcp.data) print http.uri except: print 'issue' continue f.close() While it seems to effectively parse most of the packets, I'm receiving a NeedData("premature end of headers") exception on some.
They appear to be valid packets within WireShark, so I'm a bit confused as to why the exceptions are being thrown. Extracting data payload from pcap capture. Packet analysis tools and methodology (Part 1) There are untold billions of packets flying around the web today.
A great many of them are of malicious intent. A prelude to malicious activity is often the port scan. We will learn about some of the more popular types of port scans in existence today, and the tools used for them. If you would like to see the other articles in this series please read Port scanners and scan types When one thinks of the internet several things come to mind readily. Teledyne LeCroy - Software Downloads. Using Protocol Analyzers – Saleae. Protocol Analyzers decode data that has been encoded according to a particular protocol, such as SPI or I2C.
The Logic software currently offers 23 different protocol analyzers. Adding Protocol AnalyzersTo add a Protocol Analyzer, click the Plus button on the Analyzers sidebar on the right of the software. Analyzer SettingsDifferent Analyzers require different settings. All protocol analyzers require you to specify which channels should be used for specific inputs used by the protocol. If, after running a protocol analyzer, you notice that it doesn't work or doesn't display correctly, you may want to try editing the settings.
To edit the settings for an existing analyzer, find that analyzer in the Analyzers panel on the right of the software. After editing your analyzer settings, the analyzer will re-run against any data you have collected, and will update all results. Changing the Global Radix (Hex, Decimal, etc)By default, all protocol analyzers will use the global radix settings. Download VisualEther Protocol Analyzer. Download and install the following: VisualEther 6.1.102 • 5.6 MB • February 28, 2015 minimum requirements Pentium class processor running Windows 8, Windows 7 or Windows Vista. 20 MB disk space. Sequence Diagrams from Wireshark PCAP. Video tutorials | download free trial | buy now visually debug protocol interactions summarize Wireshark output... Define templates to select messages and the fields to be included in the generated diagrams.
VisualEther analyzes the Wireshark output to generate documents that match the defined template. The template is defined as a simple XML file. PCAP Analysis, Forensics, Malware, Exploits and Traffic Samples and Challenges. Basic Bro Language References. Finding simple examples of Bro language features is somewhat difficult: the scripts that come packaged with Bro are written by experts in the language and are quite idiomatic. Here are some of the basic Bro language references I've found so far.
In upcoming blog posts, I'll show some "Baby Bro" that is even more basic than these examples. Untitled. Base/protocols/conn/main.bro — Bro 2.1 documentation. Analyst Scrapbook: A Bro script to extract artifacts from HTTP. The past few days I've been revisiting Bro (it has been awhile) for doing analysis and specific tasks when analyzing traffic dumps. Specifically of interest was carving out artifacts of interest (i.e., executables). Built into the base install of Bro is the "protocols/http/file-extract.bro" Bro script that allows you to redefine the "extract_file_types" variable to pull out files from HTTP sessions that match a specific MIME type.
However, I wanted a more flexible Bro script to also extract out files that match magic bytes or are to a URL with a specific file extension - as well as having whitelisting functionality so that Windows Update, etc. are not constantly being stored to disk. IP in IP encapsulation. Packet Sniffer and Protocol Analyzer. If you are looking for a network monitoring solution for your company or home LAN, CommView is the right tool. CommView is a powerful packet sniffer, network monitor, and protocol analyzer designed for LAN administrators, security professionals, network programmers, home users ... virtually anyone who wants a full picture of the traffic flowing through a PC or LAN segment, dial-up or ADSL connection.
The intuitive user interface and a set of powerful functions make CommView invaluable for both networking professionals and those who are new to networking. CommView allows you to examine, save, filter, import and export captured packets, view protocol decodes down to the lowest layer with full analysis of over 70 widespread protocols. The program can display vital statistics, such as IP connections, protocols distribution charts, graphical conversation matrices based on MAC and IP addresses, and other important data. CommView is brought to you by TamoSoft. TMA portal » Topics » Resources » Tools » TracesPlay – fast and simple way to access network data - European research portal on traffic monitoring and analysis. Caesar0301/awesome-pcaptools. Packet Sniffing and Injecting - Backtrack Tutorials. S Blog » Analyzing PCAP Files!
Now, on a switched network you can’t just fire up your sniffer, and expect to capture all the traffic. Four ways to extract files from pcaps - Black Bytes. The Spy Files: Extracting Word Documents from a Packet Capture. For anyone interested in network security and pen testing stuff, Wireshark is the tool to get, as it reveals pretty much everything about a network, the hosts and active services present, traffic volumes, payloads and sometimes login details as well.
Packet Data Analysis (Traffic Analysis Tool for Packet over IP) Tools for extracting files from pcaps. Forensics: Reconstructing Data from Pcap Files. Sometimes during forensics investigations, it can be useful to recover deleted or temporary files transferred by users and/or processes with protocols like FTP or HTTP.
Pcap-parser. Jon.oberheide.org - blog - dpkt tutorial #2: parsing a pcap file. Interpreting the packets. Quick and dirty packet capture data extraction. Pulling binaries from pcaps. PCAP File Carving and automated analysis. PCAP from another point of view. Geek Speak: Deep Packet Analysis - Untangling t... Sharppcap - Howto convert to string and read data from TCP packet. Pcapfix - online pcap / pcapng repair service. Tutorial 1 - creating IP fragment reassembler jNetPcap OpenSource. WinDivert 1.1: Windows Packet Divert.
Bit-Twist: Libpcap-based Ethernet packet generator. 2.2 Dissecting a Network Packet. Tools for extracting files from pcaps. Forensics: Reconstructing Data from Pcap Files. Links. Pcap.Net - Home. Pcap Software - Free Download Pcap.