

Virtual Networking 101: Understanding VMware Networking. May 30, 2012By Petra Jorgenson On a basic, structural level, virtual networks in VMware aren’t that different from physical networks; vSphere is designed to mimic the functions of a physical network, so a lot of the network hardware you’ll find in the real world, you’ll find virtualized in VMware.
If you understand how physical networks operate, then understanding virtual networking shouldn’t be too difficult. Before jumping into an explanation of how VMware handles virtual networking, I’ll first provide a quick refresher of the basic equipment that makes up a physical network. If you already have a firm understanding of how networking works, then you can skip the following paragraph. To connect to a network, a computer must be network-capable, meaning that it must have a working network interface controller (NIC), also known as a network card or network adapter, installed.
In VMware, switches are used to establish a connection between the virtual network and the physical network. RFC 6020 - YANG - A Data Modeling Language for the Network Configuration Protocol (NETCONF) [Docs] [txt|pdf] [draft-ietf-netmod...]

[Diff1] [Diff2] [Errata] PROPOSED STANDARD Errata Exist Internet Engineering Task Force (IETF) M. Bjorklund, Ed. Useful mininet setups. Mininet is a network emulation platform that is very useful to test SDN applications that you build.
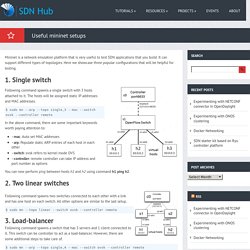
It can support different types of topologies. Here we showcase three popular configurations that will be helpful for testing. 1. Single switch Following command spawns a single switch with 3 hosts attached to it. . $ sudo mn --arp --topo single,3 --mac --switch ovsk --controller remote In the above command, there are some important keywords worth paying attention to: –mac: Auto set MAC addresses–arp: Populate static ARP entries of each host in each other–switch: ovsk refers to kernel mode OVS–controller: remote controller can take IP address and port number as options You can now perform ping between hosts h1 and h2 using command h1 ping h2. 2.
Following command spawns two switches connected to each other with a link and has one host on each switch. An Update on Using GRE Tunnels with Open vSwitch · Scott's Weblog · The weblog of an IT pro specializing in virtualization, networking, open source, and cloud computing. 22 November 2013 In this post, I’m going to provide an update on using GRE tunnels with Open vSwitch (OVS) to include more than 2 hosts.
I previously showed you how to use GRE tunnels with OVS to connect VMs on different hypervisor hosts, but in my testing I didn’t use this technique with more than two hypervisors. A few readers posted comments to that article asking how to extend the solution to more than 2 hypervisors, but I hadn’t had the time to test anything more. Now, as a result of some related work I’ve been doing, I have an update on using this technique for more than two hosts. If you didn’t read the post on using GRE tunnels with OVS, go back and read that now. Is an open source network virtualization platform for the cloud. – Architecture Documentation. This chapter provides an overview of the OpenContrail System – an extensible platform for Software Defined Networking (SDN).
All of the main concepts are briefly introduced in this chapter and described in more detail in the remainder of this document. OpenContrail is an extensible system that can be used for multiple networking use cases but there are two primary drivers of the architecture: The Private Cloud, the Virtual Private Cloud (VPC), and the Infrastructure as a Service (IaaS) use cases all involve a multi-tenant virtualized data centers. In each of these use cases multiple tenants in a data center share the same physical resources (physical servers, physical storage, physical network).
Ethernet VPN (EVPN) and Provider Backbone Bridging-EVPN: Next Generation Solutions for MPLS-based Ethernet Services. Ethernet VPN (EVPN) and Provider Backbone Bridging EVPN (PBB-EVPN) are next generation solutions that provide Ethernet multipoint services over MPLS networks.

EVPN is different compared to existing Virtual Private LAN Service (VPLS) offerings due to its use of control-plane based MAC learning over the core. EVPN has been designed from the ground up to handle sophisticated access redundancy scenarios, per-flow load balancing, and operational simplicity. PBB-EVPN inherits all of the benefits of EVPN, while combining PBB (IEEE 802.1ah) and EVPN functions in a single node.
This allows PBB-EVPN to simplify control-plane operation in the core, provide faster convergence and enhance scalability, when compared to EVPN. Generic Routing Encapsulation. Example uses[edit] In conjunction with PPTP to create VPNs.In conjunction with IPsec VPNs to allow passing of routing information between connected networks.In mobility protocols.In A8/A10 interfaces to encapsulate IP data to/from Packet Control Function (PCF).Linux and BSD can establish ad-hoc IP over GRE tunnels which are interoperable with Cisco equipment.Distributed denial of service (DDoS) protected appliance to an unprotected endpoint.
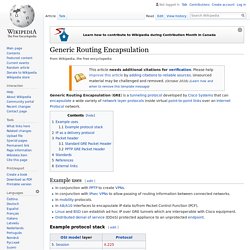
Example protocol stack[edit] Based on the principles of protocol layering in OSI, protocol encapsulation, not specifically GRE, breaks the layering order. It may be viewed as a separator between two different protocol stacks, one acting as a carrier for another. Draft-fang-l3vpn-virtual-ce-03 - BGP IP MPLS VPN Virtual CE. [Docs] [txt|pdf] [Tracker] [Email] [Diff1] [Diff2] [Nits] Versions: 00 01 02 03 INTERNET-DRAFT Luyuan Fang Intended Status: Standards track Microsoft Expires: January 4, 2015 John Evans David Ward Rex Fernando Cisco Ning So Vinci Systems Nabil Bitar Verizon Maria Napierala AT&T July 4, 2014 Abstract This document describes the architecture and solutions of using virtual Customer Edge (vCE) of BGP IP MPLS VPN.

The solution is aimed at providing efficient service delivery capability through CE virtualization, and is especially beneficial in virtual Private Cloud (vPC) environments when extending IP MPLS VPN into tenant virtual Data Center containers. This document includes: BGP IP MPLS VPN virtual CE architecture; Control plane and forwarding options; Data Center orchestration processes; integration with existing WAN enterprise VPNs; management capability requirements; and security considerations. The solution is generally applicable to any BGP IP VPN deployment. L. L. L. 1. L. L. L. 2. RFC 7432 - BGP MPLS-Based Ethernet VPN. [Docs] [txt|pdf] [draft-ietf-l2vpn-...]

[Diff1] [Diff2] [IPR] PROPOSED STANDARD Internet Engineering Task Force (IETF) A. Sajassi, Ed. Request for Comments: 7432 Cisco Category: Standards Track R. Network Virtualization Overlays (nvo3) - Documents. Virtual overlay networks: Tunneling protocols enable multi-tenancy. Virtual overlay networks have taken center stage as data center managers seek networking solutions that better... support VM provisioning, enable scalability and improve automation.
A virtual overlay network -- one form of network virtualization -- uses tunneling protocols to form paths between software-based network agents in hypervisors running on servers. Virtual overlay network software separates the virtual network from the underlying physical network hardware, enabling provisioning of virtual networks and accompanying services between servers in the data center. This means that virtual networks can be spun up on demand to support specific virtual workloads, for example.
RFC 7209 - Requirements for Ethernet VPN (EVPN) [Docs] [txt|pdf] [draft-ietf-l2vpn-...] [Diff1] [Diff2] INFORMATIONAL Internet Engineering Task Force (IETF) A. Sajassi Request for Comments: 7209 Cisco Category: Informational R. Aggarwal ISSN: 2070-1721 Arktan J. Uttaro AT&T N. RFC 7209 Requirements for Ethernet VPN May 2014 Copyright Notice Copyright (c) 2014 IETF Trust and the persons identified as the document authors. EVPN Overview. An Ethernet VPN (EVPN) enables you to connect a group of dispersed customer sites using a Layer 2 virtual bridge. As with other types of VPNs, an EVPN is comprised of customer edge (CE) devices (host, router, or switch) connected to provider edge (PE) devices.
The PE devices can include an MPLS edge switch (MES) that acts at the edge of the MPLS infrastructure. Either an MX Series 3D Universal Edge Router or a standalone EX9200 switch (Junos release 14.2) can be configured to act as an MES. You can deploy multiple EVPNs within the service provider’s network, each providing network connectivity to customers while ensuring that the traffic sharing that network remains private. Figure 1 illustrates a typical EVPN deployment. List of router and firewall distributions. Route Selection in Cisco Routers. Introduction One of the intriguing aspects of Cisco routers, especially for those new to routing, is how the router chooses which route is the best among those presented by routing protocols, manual configuration, and various other means.
While route selection is much simpler than you might imagine, to understand it completely requires some knowledge about the way Cisco routers work. Prerequisites Requirements There are no specific prerequisites for this document. Components Used This document is not restricted to specific software and hardware versions. Conventions For more information on document conventions, see the Cisco Technical Tips Conventions. Processes Involved There are three processes involved in building and maintaining the routing table in a Cisco router: Let's examine the interaction between the routing protocols and the routing table to understand how the routing table is built.
Building the Routing Table The main considerations while building the routing table are: Backup Routes. NETCONF YANG tutorial.