

U.S. developing sanctions against China over cyberthefts. The Obama administration is developing a package of unprecedented economic sanctions against Chinese companies and individuals who have benefited from their government’s cybertheft of valuable U.S. trade secrets.
The U.S. government has not yet decided whether to issue these sanctions, but a final call is expected soon — perhaps even within the next two weeks, according to several administration officials, who spoke on the condition of anonymity to discuss internal deliberations. Issuing sanctions would represent a significant expansion in the administration’s public response to the rising wave of cyber-economic espionage initiated by Chinese hackers, who officials say have stolen everything from nuclear power plant designs to search engine source code to confidential negotiating positions of energy companies. Any action would also come at a particularly sensitive moment between the world’s two biggest economies. The sanctions would be a second major shot at China on the issue.
Krebs on Security. Katherine Archuleta, Director of Personnel Agency, Resigns. WASHINGTON — Katherine Archuleta, the director of the Office of Personnel Management, resigned under pressure on Friday, one day after the government revealed that two sweeping cyberintrusions at the agency had resulted in the theft of the personal information of more than 22 million people, including those who had applied for sensitive security clearances.
Ms. Archuleta went to the White House on Friday morning to inform President Obama that she was stepping down immediately. She said later in a statement that she felt new leadership was needed at the federal personnel agency to enable it to “move beyond the current challenges.” To see the full article, subscribe here. Correction: July 10, 2015 An earlier version of this article misstated the number of people affected by cyberattacks on the Office of Personnel Management. Ms. WikiLeaks. Comment l’Arabie Saoudite promeut l’islamisme à l’échelle planétaire. Les logiciels espions sont-ils des armes ? Le Monde.fr | • Mis à jour le | Par Florian Reynaud « Hacking Team devrait être traité comme un vendeur de sandwichs. » L’échange de mails, repéré par le site spécialisé The Intercept, ferait rire jaune les associations défenseurs des droits de l’homme.
Car cette phrase est tirée d’un e-mail envoyé par une avocate consultante à la direction de l’entreprise Hacking Team, société italienne qui vend des logiciels espions - et victime d’un piratage massif il y a une semaine : l’intégralité de ses documents internes et e-mails ont été publiés en ligne. Hacking Team est loin de vendre des sandwichs – ses logiciels de surveillance, dont le plus célèbre est Galileo, sont très sophistiqués.
Des produits qui peuvent être assimilés à des armes – et donc soumis à un contrôle strict, et même à des interdictions de vente pour des pays comme le Soudan ou encore l’Erythrée, visés par des embargos européens ou des Nations unies. Une classification qui évolue lentement Ce que dit la législation européenne. Countries are supposed to spy on each other—that’s why the US won’t blame China for hacking federal files. The U.S.
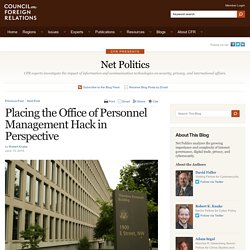
Office of Personnel Management building in Washington June 5, 2015. In the latest in a string of intrusions into U.S. agencies' high-tech systems, the Office of Personnel Management (OPM) suffered what appeared to be one of the largest breaches of information ever on government workers. (Gary Cameron/Reuters). Part of the reason I am a bit blasé about the Office of Personnel Management hack, is if the Chinese government is indeed behind it, it’s not by any stretch the most dastardly thing they have done in cyberspace. Cinq questions sur Ulcan, le hacker franco-israélien. Grégory Chelli, plus connu sous son pseudo Ulcan, a revendiqué, jeudi 9 octobre, sur sa page Facebook le piratage des sites Internet de France Info et de France Inter, qu'il accuse de « ne respecter ni la présomption d'innocence, ni les droits de réponse », de « mentir » ou de « diffamer » quand « il s'agit des juifs, d'Israël ou de moi ».
Le hacker franco-israélien a également menacé la maire de Lille, Martine Aubry. « J’ai également trouvé l’adresse de Martine Aubry et son numéro, mais j’ai pas encore décidé quelle sanction serait appropriée pour elle », a-t-il écrit. Une attaque qui intervient deux jours après le vote par les élus lillois de la mise en sommeil du jumelage de la capitale du Nord-Pas-de-Calais avec la ville de Safed, rapporte Metronews Lille. Countries are supposed to spy on each other—that’s why the US won’t blame China for hacking federal files. Visé par les tentatives d’intimidation du dénommé Ulcan. Le dénommé Grégory Chelli alias Ulcan a récidivé.
Le directeur de Politis, Denis Sieffert a été victime, dans la nuit du 17 au 18 juin, d’une dénonciation mensongère qui a entrainé une intervention de la police à son domicile. Cela, après avoir reçu plusieurs appels anonymes. Exclusive: Inside Washington's Quest to Bring Down Edward Snowden. A bipartisan group of Washington lawmakers solicited details from Pentagon officials that they could use to "damage" former NSA contractor Edward Snowden's "credibility in the press and the court of public opinion.
" That's according to declassified government documents obtained exclusively by VICE News in response to a long-running Freedom of Information Act (FOIA) lawsuit. The lawmakers' requests for information were made in December 2013 and again in February 2014, following classified briefings top officials at the Defense Intelligence Agency (DIA) held for oversight committees in the House and Senate about a DIA assessment of the alleged damage to national security caused by Snowden's leak of top-secret documents to journalists Glenn Greenwald, Barton Gellman, and Laura Poitras. Chinese hack compromised security-clearance database. The Chinese breach of the Office of Personnel Management network was wider than first acknowledged, and officials said Friday that a database holding sensitive security clearance information on millions of federal employees and contractors also was compromised.
In an announcement, OPM said that investigators concluded this week with “a high degree of confidence” that the agency’s systems containing information related to the background investigations of “current, former and prospective” federal employees, and others for whom a background check was conducted, were breached. OPM is assessing how many people were affected, spokesman Samuel Schumach said. “Once we have conclusive information about the breach, we will announce a notification plan for individuals whose information is determined to have been compromised,” he said.
The announcement of the hack of the security-clearance database comes a week after OPM disclosed that another personnel system had been compromised. How Russians hacked the White House. While the White House has said the breach only affected an unclassified system, that description belies the seriousness of the intrusion.
The hackers had access to sensitive information such as real-time non-public details of the president's schedule. While such information is not classified, it is still highly sensitive and prized by foreign intelligence agencies, U.S. officials say. The White House in October said it noticed suspicious activity in the unclassified network that serves the executive office of the president. The system has been shut down periodically to allow for security upgrades. The FBI, Secret Service and U.S. intelligence agencies are all involved in investigating the breach, which they consider among the most sophisticated attacks ever launched against U.S. government systems. National Security Council spokesman Mark Stroh didn't confirm the Russian hack, but he did say that "any such activity is something we take very seriously.
" Neither the U.S. Sunday Times Snowden Story is Journalism at its Worst. (updated below) Western journalists claim that the big lesson they learned from their key role in selling the Iraq War to the public is that it’s hideous, corrupt and often dangerous journalism to give anonymity to government officials to let them propagandize the public, then uncritically accept those anonymously voiced claims as Truth.

But they’ve learned no such lesson. That tactic continues to be the staple of how major U.S. and British media outlets “report,” especially in the national security area. And journalists who read such reports continue to treat self-serving decrees by unnamed, unseen officials — laundered through their media — as gospel, no matter how dubious are the claims or factually false is the reporting. We now have one of the purest examples of this dynamic. White House Weighs Responses as Scope of Federal Hack Widens. More federal personnel records have been hacked than previously reported and U.S. officials are weighing responses ranging from new counterintelligence initiatives to destroying the data in the intruders’ servers, according to people briefed on the investigation. Already considered one of the largest thefts of U.S. government personnel data in history, investigators now estimate that it may include data on as many as 14 million people, more than triple the 4 million current and former government employees reported by the Office of Personnel Management last week, according to one lawmaker who asked not to be identified when discussing the investigation.
Four others, including lawmakers and people briefed on the investigation, said the number of people whose data was stolen was significantly higher than 4 million. The hackers rifled computers unseen for months, vacuuming up huge quantities of data. Government Union U.S. Chinese hackers sought information to blackmail U.S. government workers, officials believe. The investigation into the cyberattack on computers at the U.S. Office of Personnel Management is proceeding on the theory that the hack was directed by the Chinese government and aimed at uncovering sensitive, personal information that could have been used to blackmail or bribe government employees to obtain secrets, officials said Friday. Social Security numbers, email addresses, job performance reviews and other personal information of about four million government workers were siphoned out of the computer servers, said the officials, who spoke on condition of anonymity to discuss internal assessments of the breach.
The information obtained in the attack could be useful on its own and also could be used to craft fake emails that would entice government workers to open attachments that would infect their computers with malicious software designed to bleed additional information off federal computers. Computer security experts call such attacks “spear-phishing.” Aspects stratégiques du cyberespace. Définition, enjeux. LE CYBERESPACE est un mot en vogue ce qui peut susciter une certaine défiance : s’agit-il encore d’un produit de publicitaires ? Pourtant, à écouter tous les responsables publics et privés expliquer qu’il constitue un des défis majeurs de notre époque, il faut s’interroger et aller au-delà de la circonspection initiale. Surtout quand on entend le préfixe « cyber » associé à des sujets de préoccupations plus traditionnels comme la sécurité ou la défense.
En effet, le cyberespace est non seulement nouveau et prégnant, mais il emporte des aspects stratégiques importants. Pour le comprendre, l’étude des caractéristiques stratégiques de ce cyberespace précédera la description des opportunités qu’il présente pour les différents acteurs, qui vont utiliser de nouvelles règles stratégiques. I. La première caractéristique du cyberspace est son universalité : non seulement le cyber [1] est désormais à la surface du globe, mais il est également présent dans tous les aspects de nos vies. Penser les réseaux. Je suis heureux de vous annoncer la parution du petit dernier ouvrage que j'ai dirigé : Penser les réseaux, une approche stratégique.
Il s'agit des actes d'un colloque tenu en juin 2013 augmentés de quelques textes qui permettent de construire un ouvrage complet et cohérent. Trois thèmes se succèdent : approche théorique, perspectives militaires et stratégique, point de vue techno-économique. Au fond, il s'agit de penser la notion de réseau avant d'aller voir du côté du cyber et de l'informatique même si cette approche est aussi présente, bien sûr. Avec des textes de l’amiral Arnaud Coustillère, Philippe Davadie, Frederick Douzet, Eric Hazane, François-Bernard Huyghe, Olivier Kempf, Colin L’Hermet, Dominique Lacroix, Jarno Limnèll, N. Réseaux sociaux, géopolitique et conflit.
Cyberstratégie. Carte. Hiérarchie de l'Internet, acteurs et renseignement - Monde. Wikileaks Actu Francophone. L’Internet nous a tous rapproché les uns des autres… malheureusement. The Conversation, 21 octobre 2014 Par Siraj Ahmed Shaikh Qui est dans votre réseau, en train de vérifier vos données? L'ennemi à l'ère numérique - F.B. Huyghe. L'ennemi à l'ère numérique.