

The 30 Minute Regex Tutorial. Expresso 2.1C - 328 Kb Learning .NET Regular Expressions with Expresso Did you ever wonder what Regular Expressions are all about and want to gain a basic understanding quickly?
My goal is to get you up and running with a basic understanding of regular expressions within 30 minutes. The reality is that regular expressions aren't as complex as they look. The best way to learn is to start writing and experimenting. What the Heck is a Regular Expression Anyway? I'm sure you are familiar with the use of "wildcard" characters for pattern matching. In writing programs or web pages that manipulate text, it is frequently necessary to locate strings that match complex patterns.
A good way to learn the arcane syntax of regular expressions is by starting with examples and then experimenting with your own creations. Let's get started! Some Simple Examples Searching for Elvis. Regex ve Performans İpuçları – Otomatik Cache. Merhaba Arkadaşlar, Şu an yazıyı hazırlamaya çalıştığım an İstanbul’ un tarihinde gördüğü en sıcak gecelerden birisine denk gelmekte sanırım. Gündüz yaklaşık olarak 53 derece olarak hissedilen sıcaklığı ofisteki kuvvetli klimalar sayesinde fazla hissetmedik belki ama eve dönüş yolunda, gerek otobüslerde gerekse minibüs veya diğer toplu taşıma araçlarında fazlasıyla hissettiğimize eminim Gece çökmesine ve balkonda oturmama rağmen ne yazık ki yapraklar bile sıcak dolayısıyla kendinden geçmiş durumda ve bu nedenle sallanmak dahi istemiyorlar.
Hal böyle olunca serinletici esintilerinde tatile çıktıklarını ifade edebilirim. Acaba tüm bu yaşadıklarımız, garip olan bu yaz mevsimi, yağmurlarla geçen günler ve aşırı sıcaklar gerçekten de Küresel Isınmanın sonuçların mı? ASP.NET 1.1 Security Guidelines - Input Validation - Guidance Share. From Guidance Share - J.D. Meier, Alex Mackman, Michael Dunner, Srinath Vasireddy, Ray Escamilla and Anandha Murukan Constrain, Then Sanitize Start by constraining input and check for known good data by validating for type, length, format, and range. Sometimes you also need to sanitize input and make potentially malicious input safe. Table Options for Constraining and Sanitizing Data References See Building Secure ASP.NET Pages and Controls at Use Regular Expressions for Input Validation You can use regular expressions to restrict the range of valid characters, to strip unwanted characters, and to perform length and format checks.
How To: Protect From Injection Attacks in ASP.NET. MSDN Library patterns & practices Retired Solution Development Fundamentals Security Security Guidance for Applications.
Keeping Web Users Safe By Sanitizing Input Data. Advertisement In my last article, I spoke about several common mistakes that show up in web applications.
Of these, the one that causes the most trouble is insufficient input validation/sanitization. In this article, I’m joined by my colleague Peter (evilops) Ellehauge in looking at input filtering in more depth while picking on a few real examples that we’ve seen around the web. As you’ll see from the examples below, insufficient input validation can result in various kinds of code injection including XSS, and in some cases can be used to phish user credentials or spread malware. To start with, we’ll take an example[1] from one of the most discussed websites today.
Input Validation using Regular Expressions. Input Validation using Regular Expressions Posted by Joe Basirico on Mon, Mar 28, 2011 @ 08:00 AM Input validation is your first line of defense when creating a secure application, but it's often done insufficiently, in a place that is easy to bypass, or simply not done at all.
Since this is a common issue I see in our assessments and something that has such a great impact on security I'd like to spend a bit of time outlining input validation best practices and give you some concrete examples of how to do it well. Input validation is the practice of limiting the data that is processed by your application to the subset that you know you can handle. This means going beyond simple data types and diving deeply into understanding the ideal data type, range, format and length for each piece of data. Whitelist or Blacklist? Validating User Input in ASP.NET Web Pages Sites. How to Prevent Cross-Site Scripting in ASP.NET. How to Prevent Cross-Site Scripting in ASP.NET Posted by Serge Truth on Tue, Jan 10, 2012 @ 08:00 AM Summary This How to shows how you can help protect your ASP.NET applications from cross-site scripting attacks by using proper input validation techniques and by encoding the output.
It also describes a number of other protection mechanisms that you can use in addition to these two main countermeasures. Cross-site scripting (XSS) attacks exploit vulnerabilities in Web page validation by injecting client-side script code. Contents. Page.IsValid and Validate - Raj Kaimal. ASP.net ships with a couple of validator controls that allow you to determine whether the value of the input controls they are validating is valid.
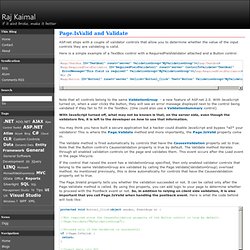
Here is a simple example of a TextBox control with a RequiredFieldValidator attached and a Button control. <asp:RequiredFieldValidator ID="RequiredFieldValidator1" runat="server" ControlToValidate="TextBox1" ErrorMessage="This field is required! " ValidationGroup="MyValidationGroup"></asp:RequiredFieldValidator> Note that all controls belong to the same ValidationGroup - a new feature of ASP.net 2.0. With JavaScript turned off, what may not be known is that, on the server side, even though the validators fire, it is left to the developer on how to use that information.
You may think you have built a secure application but a hacker could disable JavaScript and bypass *all* your validators!