

The Fabric of the Cosmos. PBS airdate: 11/16/2011 NARRATOR: Lying just beneath everyday reality is a breathtaking world, where much of what we perceive about the universe is wrong.
Physicist and best-selling author Brian Greene takes you on a journey that bends the rules of human experience. BRIAN GREENE (Columbia University): Why don't we ever see events unfold in reverse order? According to the laws of physics, this can happen. NARRATOR: It's a world that comes to light as we probe the most extreme realms of the cosmos, from black holes to the Big Bang to the very heart of matter, itself. BRIAN GREENE: I'm going to have what he's having. NARRATOR: Here, our universe may be one of numerous parallel realities, the three-dimensional world, merely a mirage; the distinction between past, present and future, just an illusion. BRIAN GREENE: But how could this be?
DAVID GROSS: Does it bother us? Paul Falstad. Www.math.sc.edu/~cooper/math778C/abct.pdf. Www.cs.utexas.edu/~eberlein/cs301k/propLogic.pdf. Intro to JS: Drawing & Animation. The relationship between Sin, Cos, and the right triangle. Dual Boot Tutorial - Install OS X And Windows On Same PC/Hackintosh. Memory leak. A memory leak, in computer science (or leakage, in this context), occurs when a computer program consumes memory but is unable to release it back to the operating system.
A memory leak has symptoms similar to a number of other problems (see below) and generally can only be diagnosed by a programmer with access to the program source code; however, many people refer to any unwanted increase in memory usage as a memory leak, though this is not strictly accurate. Contents Consequences Memory leaks may not be serious or even detectable by normal means.
In modern operating systems, normal memory used by an application is released when the application terminates. Leaks that are much more serious include: An example of memory leak The following example, written in pseudocode, is intended to show how a memory leak can come about, and its effects, without needing any programming knowledge.
Cases like this wouldn't usually have any immediate effects. Programming Tetris by first building a logic gate, then a computer, then… Electric circuit - definition of electric circuit by the Free Online Dictionary. Wireless mesh network. Diagram showing a possible configuration for a wireless mesh network, connected upstream via a VSAT link (click to enlarge) History[edit] Network structures[edit] Architecture[edit] Wireless mesh architecture is a first step towards providing cost effective and dynamic high-bandwidth networks over a specific coverage area. Wireless mesh architectures infrastructure is, in effect, a router network minus the cabling between nodes.
Comparison of programming languages. Programming languages are used for controlling the behavior of a machine (often a computer).
Like natural languages, programming languages conform to rules for syntax and semantics. There are thousands of programming languages[1] and new ones are created every year. Few languages ever become sufficiently popular that they are used by more than a few people, but professional programmers may use dozens of languages in a career. Programmable Logic. Can I Hackintosh My Laptop? "Never.
You can never hackintosh a laptop and have it work just as well as a real Mac. If there's anything that Apple does very well, it's make some slick portable hardware. No other PC laptop is going to run Mac OS X as well, regardless of how compatible the hardware is. " Sorry - I have to call this on obvious silliness. There's nothing inside a Mac that's magical or unicorn based. The reason Macs work 'better' at being Macs than a Hackintosh is really, really simple: Apple builds their computers AND their OS AND their drivers. So, back to this assertion. The one exception? Macs were the first computer to use UEFI (or more accurately - just EFI).
Having the exact same chip won't help - you'd need the PKI certificate in the chip and you can't read that back out. So the first thing people do is kill the KEXT that handles this task. Now, for any OTHER PC, the problem gets worse. Planet Source Code home page.
Stock Prediction Neural Network. Gradient descent. Gradient descent is a first-order optimization algorithm.
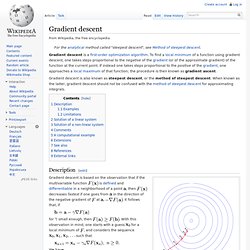
To find a local minimum of a function using gradient descent, one takes steps proportional to the negative of the gradient (or of the approximate gradient) of the function at the current point. If instead one takes steps proportional to the positive of the gradient, one approaches a local maximum of that function; the procedure is then known as gradient ascent. Gradient descent is also known as steepest descent, or the method of steepest descent.
When known as the latter, gradient descent should not be confused with the method of steepest descent for approximating integrals. Description[edit] Illustration of gradient descent with step size proportional to the gradient. Gradient descent is based on the observation that if the multivariable function.