

Twitter. RFC 7381 - Enterprise IPv6 Deployment Guidelines. [Docs] [txt|pdf] INFORMATIONAL Internet Engineering Task Force (IETF) K.

Chittimaneni Request for Comments: 7381 Dropbox, Inc. Category: Informational T. Chown ISSN: 2070-1721 University of Southampton L. Howard Time Warner Cable V. RFC 7381 Enterprise IPv6 Deployment October 2014 Copyright Notice Copyright (c) 2014 IETF Trust and the persons identified as the document authors. NAT64 and DNS64 in 30 minutes.
15 Jahre Internet Protocol Version 6. Seit der Verabschiedung des IPv6-Standards RFC 2460 im Dezember 1998 hat sich viel getan – Anlass genug, den Blick auf die holprige Geschichte und die Gegenwart des "neuen" Internet-Protokolls zu richten.
Kritisch betrachtet ist IPv6 bisher nicht gerade eine Erfolgsgeschichte, und das bezieht sich nicht nur auf seine äußerst zähe Einführung, sondern auch auf die zahlreichen Ungereimtheiten, die es enthält. Stellenweise erweckt das renovierte Protokoll den Anschein, dass die Designer wenig aus den Fehlern der Vergangenheit gelernt haben, besonders unter Sicherheitsaspekten. What Happens if You're IPv4 Only. We had a pretty good discussion on this last month with Owen from HE, Asia and other parts of the world that don't have IPv4 space to hoard are already moving heavily into IPv6.
What's most important to the migration for ARIN is content being available on IPv6. Even at 50% growth YoY it's still only 1.5% of the internet's traffic. What we need is more switch over to IPv6 dates for the content guys to share that risk. Yea, no one knows when your particular org will run out, or how much gray market space will be available here in NA, but it's a painful process to get your network over to IPv6, not only from a network perspective, but from a product and OSS/BSS perspective as well. Anyone who's hasn't deployed and not planning for it is either blind, very short sited, or not in charge of having worry about it. And no, I'm still not a fan of LSN. The IPv6 wave is moving ... just not as expected. I loved my v6 wave diagram.
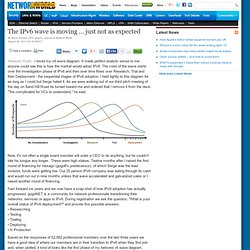
It made perfect analytic sense to me; anyone could see this is how the market would adopt IPv6. The crest of the wave starts over the Investigation phase of IPv6 and then over time flows over Research, Trial and then Deployment - the sequential stages of IPv6 adoption. Core Networking and Security: Should You Allow Inbound E-mail Over IPv6?
ARIN: Great video for #IPv6 begi... Log the source ports of HTTP sessions. You’re probably tired of this story by now: public IPv4 addresses are running out, lots of content is available only over IPv4, and so the service providers use NAT to give new clients (with no public IPv4 address) access to old content.
It doesn’t matter which NAT variant the service provider is using, be it Carrier Grade Nat (CGN), NAT64, DS-Lite or A+P, the crucial problem is always the same: multiple users are hidden behind a single source IP address. If you’re running a public web-based service (anything from non-hosted private blog to e-commerce solutions), you’re probably logging the HTTP requests made by the clients. Best case, you use the logs to monitor your web traffic, worst case, you can use them to help law enforcement track down the intruders ... but not if the intruders were hiding behind NAT. RFC 6302 nicely documents the logging requirements (just in case someone asks you who said the source TCP port should be logged). Securing IPv6. In the previous installment of our series of IPv6 security posts, we covered some of the ways addressing has changed in IPv6 compared to IPv4.
In this post, we’ll talk about some of the things to consider when securing IPv6 compared to IPv4. Before digging into this topic, however, it is important to remember that while IPv6 may have different security concerns than IPv4, it is not necessarily any more secure than IPv4. Furthermore, the post will focus on those aspects that are different or unique to IPv6, since many of the common best practices for IPv4 networks also apply to IPv6 networks. Dual Stack Concerns First off, to support the transition from IPv4 to IPv6, many systems support both IPv4 and IPv6 traffic simultaneously, in what is known as a dual stack configuration. MITM Attack Exploits Windows IPv6 Protocols. Researchers indicate that new features in the Microsoft Windows operating system which enable IPv6 network access can potentially be exploited by a man-in-the-middle (MITM) attack.
The proof of concept was detailed by security researcher Alec Waters of the Infosec Institute, and shows that default settings in the OS protocol allow attackers to redirect information unbeknownst to the user. “All these Windows boxes will default connect to the evil router instead of the legitimate router when this parasitic overlay is running. If Microsoft didn't have that configuration by default, it would negate a lot of the effects of the attack," said Jack Koziol, program manager for the InfoSec Institute. The exploit utilizes the Stateless Address Auto Configuration (SLAAC) standard to reroute data through networks controlled by the attackers, exposing potentially sensitive data.