

Adding Tomcat to XAMPP in Linux. Ok, here is what I typed before I got bored.
Visit to download and extract the latest release to /opt/tomcat. Download the i586 Tomcat Connector binary and it's verification signature here, rename as "mod_jk.so" and copy to lampp/modules folder. Create a file called "workers.properties" inside of the lampp/conf folder with the following content: Test HTTP API requests - Twilio Labs. Mysql - ERROR 1044 (42000): Access denied for user ''@'localhost' to database 'db' Tomcat – java.lang.OutOfMemoryError: PermGen space. Often time, Tomcat may hits the following java.lang.OutOfMemoryError: PermGen space error.
MySQL 5.5 Reference Manual.
Set up SSH for Git and Mercurial on Mac OSX/Linux - Bitbucket. Up until this point, you have been using the secure hypertext transfer protocol (HTTPS) to communicate between your local system and Bitbucket.
When you use HTTPS, you need to authenticate (supply a username and password) each time you take an action that communicates with the Bitbucket server. You can specify the username in the DVCS configuration file; you don't want to store your password there though where anyone can see it.
Java - Ant Tomcat 7 Reload FileNotFoundException. Maven in 5 Minutes. Prerequisites You must have an understanding of how to install software on your computer.
If you do not know how to do this, please ask someone at your office, school, etc or pay someone to explain this to you. The Maven mailing lists are not the best place to ask for this advice. Installation Maven is a Java tool, so you must have Java installed in order to proceed. First, download Maven and follow the installation instructions. It should print out your installed version of Maven, for example: Java Security Framework. A Realm is a component that can access application-specific security data such as users, roles, and permissions.
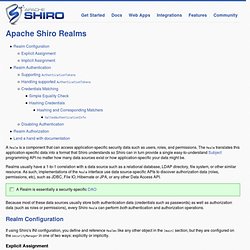
The Realm translates this application-specific data into a format that Shiro understands so Shiro can in turn provide a single easy-to-understand Subject programming API no matter how many data sources exist or how application-specific your data might be. Realms usually have a 1-to-1 correlation with a data source such as a relational database, LDAP directory, file system, or other similar resource.
As such, implementations of the Realm interface use data source-specific APIs to discover authorization data (roles, permissions, etc), such as JDBC, File IO, Hibernate or JPA, or any other Data Access API. Because most of these data sources usually store both authentication data (credentials such as passwords) as well as authorization data (such as roles or permissions), every Shiro Realm can perform both authentication and authorization operations.
Java Security Framework. Authentication is the process of identity verification-- you are trying to prove a user is who they say they are.

To do so, a user needs to provide some sort of proof of identity that your system understands and trust. The goal of this guide is to walk you through how Authentication in Java is performed in Shiro. If you haven't already please take moment and go through Shiro's 10 Minute Tutorial so that you get a basic understanding of how to work with Shiro. Terminology you'll need Subject - Security specific user 'view' of an application user. How to Authenticate in Java with Shiro In Shiro's framework, and most every other framework for that matter, the Java authentication process can be broken up into three distinct steps.
Steps Collect the subject's principals and credentialsSubmit the principals and credentials to an authentication system.Allow access, retry authentication, or block access. JHijack. Free Development software downloads. WebScarab Getting Started. WebScarab has a large amount of functionality, and as such can be quite intimidating to the new user.
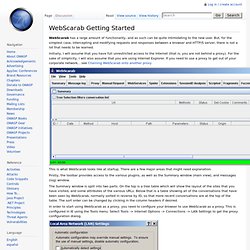
But, for the simplest case, intercepting and modifying requests and responses between a browser and HTTP/S server, there is not a lot that needs to be learned. Initially, I will assume that you have full unrestricted access to the Internet (that is, you are not behind a proxy). For the sake of simplicity, I will also assume that you are using Internet Explorer. If you need to use a proxy to get out of your corporate network, , see Chaining WebScarab onto another proxy This is what WebScarab looks like at startup. Firstly, the toolbar provides access to the various plugins, as well as the Summary window (main view), and messages (log) window. The Summary window is split into two parts. YGN Ethical Hacker Group (YEHG) Webgoat | More Trainings>> These movies show yow how WebScarab is useful in several ways.

It is a must-tool for web hacker daily. Spidering [View Online | Download ] Description: See how you generate web site tree with WebScarab's Spidering Engine. Finding Hidden Clues [View Online | Download ] Description: This is a WebGoat's lesson: Discovering Clues in HTML Comments using WebScarab's Fragments Engine. Session Analysis [View Online | Download ] Description: See how WebScarab is of great help in analyzing the stregth of Session using its SessionID Analysis Engine.