

Dynamically Unpacking Malware With Pin. A common approach that malware takes to hide itself is packing.

Sources. Buying Personal Information in the Deep Web. The criminal underground Before starting our quick tour in the criminal underground to collect information on the principal items and services offered for sale and rent, lets clarify some useful concepts.
What is the underground ecosystem? The term underground ecosystem is usually used to refer a collection of forums, websites and chat rooms that are designed with the specific intent to advantage, streamline and industrialize criminal activities. The underground ecosystem represents a portion of cyberspace that is considered vital for criminal communities, where criminals can acquire and sell tools, services and data for various kinds of illegal activities.
Ethical Hacking Training – Resources (InfoSec) Recently a team of experts from Dell SecureWorks released a report on black hat markets, titled “Underground Hacker Markets“, which reported a number of noteworthy trends, the most interesting of which is the growing interest in personal data. Shellcodes Database. Description Although these kinds of shellcode presented on this page are rarely used for real exploitations, this page lists some of them for study cases and proposes an API to search specific ones.
Thanks all for your contributions of this database but we stopped to accept shellcodes. To learn modern exploitation, checkout how to the Return Oriented Programming works. This is very straightforward to communicate with this API. Just send a simple GET method. Use "*" for multiple keywords search. Photos of an NSA “upgrade” factory show Cisco router getting implant.
A document included in the trove of National Security Agency files released with Glenn Greenwald’s book No Place to Hide details how the agency’s Tailored Access Operations (TAO) unit and other NSA employees intercept servers, routers, and other network gear being shipped to organizations targeted for surveillance and install covert implant firmware onto them before they’re delivered.
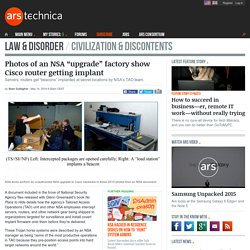
These Trojan horse systems were described by an NSA manager as being “some of the most productive operations in TAO because they pre-position access points into hard target networks around the world.” The document, a June 2010 internal newsletter article by the chief of the NSA’s Access and Target Development department (S3261) includes photos (above) of NSA employees opening the shipping box for a Cisco router and installing beacon firmware with a “load station” designed specifically for the task. Startup finds malware intrusions by keeping an eye on processor radio frequencies. PFP Cybersecurity, a startup with roots in academia and the military, seeks out malware by analyzing the performance of hardware - not software and not the behavior of devices on the network.
PFP’s system compares ongoing radio-frequency output from processors to a baseline that is established when the device is known to be performing legitimate tasks. Bwall/HashPump.
Qualys SSL Labs - Projects / SSL Server Test. Future South Gazette. Gyrophone: Recognizing Speech from Gyroscope Signals. BetterCrypto⋅org. Exploit writing tutorial part 10 : Chaining DEP with ROP – the Rubik’s[TM] Cube. Table of Contents Introduction About 3 months after finishing my previous exploit writing related tutorial, I finally found some time and fresh energy to start writing a new article.
![Exploit writing tutorial part 10 : Chaining DEP with ROP – the Rubik’s[TM] Cube](http://cdn.pearltrees.com/s/pic/th/exploit-tutorial-chaining-14952095)
Plain Text Offenders - About. Elvanderb/TCP-32764. ShellNoob 1.0 - a shellcode writing toolkit. Mmozeiko/aes-finder. Online x86 and x64 Intel Instruction Assembler. Exploit writing tutorial part 3 : SEH Based Exploits. James Lyne: Everyday cybercrime. Security Circus. Images/defcon-17/dc-17-presentations/defcon-17-joseph_mccray-adv_sql_injection.pdf. XSS Filter Evasion Cheat Sheet. Last revision (mm/dd/yy): 07/4/2018 This cheat sheet lists a series of XSS attacks that can be used to bypass certain XSS defensive filters.
Please note that input filtering is an incomplete defense for XSS which these tests can be used to illustrate. Basic XSS Test Without Filter Evasion. Interview With A Blackhat (Part 2) [Please note that this series of posts discusses criminal activities from the perspective of the criminal.
Hijacking a Facebook Account with SMS. This post will demonstrate a simple bug which will lead to a full takeover of any Facebook account, with no user interaction.
Enjoy. Facebook gives you the option of linking your mobile number with your account. This allows you to receive updates via SMS, and also means you can login using the number rather than your email address. The flaw lies in the /ajax/settings/mobile/confirm_phone.php end-point. This takes various parameters, but the two main are code, which is the verification code received via your mobile, and profile_id, which is the account to link the number to. Malware Hidden Inside JPG EXIF Headers. How to 0wn the Internet in Your Spare Time. This paper appears in the Proceedings of the 11th USENIX Security Symposium (Security '02) Also in PDF optimized for reading onlinePDF optimized for printing Abstract The ability of attackers to rapidly gain control of vast numbers of Internet hosts poses an immense risk to the overall security of the Internet.

Hackers Hut: Exploiting the heap. NextPreviousContents 11. Exploiting the heap Sometimes the buffer that overflows is not a local buffer on the stack, but a buffer obtained from malloc() and freed with free(). Let us do a small demo. Exploit the program heapbug.c: #include <stdio.h> #include <string.h> #include <stdlib.h> int main(int argc, char **argv) { char *p, *q; p = malloc(1024); q = malloc(1024); if (argc >= 2) strcpy(p, argv[1]); free(q); free(p); return 0; } Hacker uses an Android to remotely attack and hijack an airplane. The Hack in the Box (#HITB2013AMS) security conference in Amsterdam has a very interesting lineup of talks [pdf]. One that jumped out was the Aircraft Hacking: Practical Aero Series presented by Hugo Teso, a security consultant at n.runs in Germany. According to the abstract, “This presentation will be a practical demonstration on how to remotely attack and take full control of an aircraft, exposing some of the results of my three years research on the aviation security field.
The attack performed will follow the classical methodology, divided in discovery, information gathering, exploitation and post-exploitation phases. The complete attack will be accomplished remotely, without needing physical access to the target aircraft at any time, and a testing laboratory will be used to attack virtual airplanes systems. While keeping an eye on Twitter #HITB2013AMS, greatly interesting tweets started to appear as hackers who attended were excited. LinkedIn vs. password cracking. Index of /content/downloads/pdf.
Smashing the Stack for Fun and Profit by Aleph One.