

How the protection of Citadel got cracked. Recently on a forum someone requested cbcs.exe (Citadel Backconnect Server) If you want to read more about the Backconnect on Citadel, the link that g4m372 shared is cool:
Malware don't need Coffee: Inside Citadel 1.3.4.5 C&C & Builder - Botnet Control Panel. Win32/Gapz: steps of evolution. The Win32/Gapz malware family was mentioned publicly for the first time in the middle of November 2012, by the Russian antivirus company Doctor Web (Trojan.Gapz.1 infecting Windows in a new manner).
But I didn’t find the technical details about this threat in that report and so prepared a deeper analysis. Win32/Gapz uses many exploitation techniques for implementing local privilege escalation (LPE) and infecting the VBR (Volume Boot Record) and MBR (Master Boot Record) in the earliest samples seen. The first interesting finding is that the VBR infection method is really new and not something we’ve seen before in other bootkit families. And the second interesting characteristic is the method used for injecting the malicious payload into user-mode system processes.
The VBR infector changes only four bytes in bootstrap code in order to get control so as to deliver the malicious shellcode payload. What versions of MS Windows can be infected? • x64: Windows Vista SP2 and higher. Banking Trojan Targets South Korean Banks; Uses Pinterest as C&C Channel. We recently found a new banking Trojan which targeted several banks in South Korea.
This isn’t the first, though: in June last year, we saw that several online banking threats widened their range and targeted South Korean banks using various techniques. Throughout the course of monitoring similar threats, we noticed a new wave of banking Trojans targeting South Korean banks that show unusual behavior, including the use of Pinterest as their command and control (C&C) channel. Infection Via Malicious Iframe Injection This threat is currently affecting users in South Korea via compromised sites leading to exploit kits. Malware’s new target: your password manager’s password. Cyber criminals have started targeting the password managers that protect an individual's most sensitive credentials by using a keylogger to steal the master password in certain cases, according to research from data-protection company IBM Trusteer.
The research found that a configuration file, which attackers use to tailor the Citadel trojan for specific campaigns, had been modified to start up a keylogger when the user opened either Password Safe or KeePass, two open-source password managers. While malware has previously targeted the credentials stored in the password managers included in popular Web browsers, third-party password managers have typically not been targeted. While the current impact of the attack is low, the implications of the attacker’s focus is that password managers will soon come under more widespread assault, Dana Tamir, director of enterprise security for IBM Trusteer, told Ars Technica. Q1 2014: Mobile Banking Trojans Double, Surge in Bitcoin Wallet Attacks, and Cyber-Espionage Threats Back from the Dead. ABINGDON, England, April 24, 2014 /PRNewswire via COMTEX/ -- ABINGDON, England, April 24, 2014 /PRNewswire/ -- In December, Kaspersky Lab published its threat forecast for 2014.
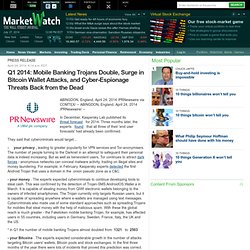
Three months later, the experts found that all three of their 'end user forecasts' had already been confirmed. Facebook Webinject Leads to iBanking Mobile Bot. iBanking is a malicious Android application that when installed on a mobile phone is able to spy on its user’s communications.
This bot has many interesting phone-specific capabilities, including capturing incoming and outgoing SMS messages, redirecting incoming voice calls, and even capturing audio using the device’s microphone. As reported by independent researcher Kafeine, this mobile application was for sale in underground forums and was used by several banking Trojans in an attempt to bypass a mobile two-factor authentication method put forth by some financial institutions.
This method, usually called “mobile transaction authorization number” (mTAN) or mToken in the financial realm, is used by several banks throughout the world to authorize banking operations, but is now also increasingly used by popular internet services such as Gmail, Facebook and Twitter. Recently, it was revealed by RSA that iBanking’s source code was leaked on underground forums. AV Labs Identifies Dangerous Zeus Banking Trojan Variant. April 3, 2014 | By Comodo AV Labs Comodo Antivirus Labs has identified a new and extremely dangerous variant of the Zeus banking Trojan.
Hackers use Zeus to launch attacks that obtain the login credentials of visitors to online banking sites and commit financial fraud. A Closer Look: Perkele Android Malware Kit. In March 2013 I wrote about Perkele , a crimeware kit designed to create malware for Android phones that can help defeat multi-factor authentication used by many banks. In this post, we’ll take a closer look at this threat, examining the malware as it is presented to the would-be victim as well as several back-end networks set up by cybercrooks who have been using mobile bots to fleece banks and their customers.
Perkele disguises itself as various Android security applications and certificates. Perkele is sold for $1,000 , and it’s made to interact with a wide variety of malware already resident on a victim’s PC. When a victim visits his bank’s Web site, the Trojan (be it Zeus or Citadel or whatever) injects malicious code into the victim’s browser, prompting the user to enter his mobile information, including phone number and OS type.
The Wild Wild Web: YouTube ads serving malware. There’s never a dull moment in the security industry, just as we heard about the latest IE 0day; one of our field security engineers in the Americas stumbled upon a YouTube link that was hosting malware.
The vulnerability is not in YouTube as such, but the ad-network seems to be the culprit in this case. We’re working with Google security team to get to the bottom of this, in the meantime some quick details about the infection below. Summary - Classic drive-by download attack, infects the user by exploiting client software vulnerabilities. Malware Research Resources. Pages Sunday, February 16, 2014 Malware Research Resources Below you will find some of my favorite malware research resources.Books:
Analyzing Environment-Aware Malware. A look at Zeus Trojan variant called Citadel evading traditional sandboxes Fighting traditional sandboxes (or dynamic analysis systems in general) typically comes in the form of detecting the analysis environment or evading analysis through means of behavior triggers as mentioned in a previous blog post: Using High-Resolution Dynamic Analysis for BHO Trigger Detection.
Some variants of the notorious Zeus trojan family use a different approach to hinder analysis: Host fingerprinting. Zeus Encryption Keys. Community Momentum is Rising! The amount of research pouring out of the Volatility community recently has been very exciting. Zeus Encryption Keys. YARA - The pattern matching swiss knife for malware researchers. YARA in a nutshell YARA is a tool aimed at (but not limited to) helping malware researchers to identify and classify malware samples.
Security Conference Ranking and Statistic. Computer Security Conference Ranking and Statistic. The State of Financial Trojans in 2013. Cuckoo Sandbox on Hardware: Preparing the hardware node for cloning. 64-Bit Zeus Banking Trojan Communicates Over Tor Network. Online banking faces a new threat. On July 18, 2013, the following post was published on a closed cybercriminal forum: The author of this post was offering a malicious program that could be used to attack “about 100 banks” by seeding add-on code onto bank websites viewed with Internet Explorer and Mozilla Firefox, with VNC connections, and other ways to attack “any bank in any country.”
Kaspersky Lab immediately began to dig deeper, and discovered that the program the malicious users were offering was Trojan-Banker.Win32/64.Neverquest.