

Coastal Courier, coastalcourier.com – news and sports for Fort Stewart, Hinesville and Ludowici. Kurzweil Accelerating Intelligence. What Chinese slowdown? Apple’s sales double in China on iPhone growth. After years of economic turmoil, a near-Grexit, a looming Brexit, and a refugee crisis that challenges the very principle of open borders, it’s safe to say that the European Union is struggling.
According to Yanis Varoufakis, Greece’s unforgettable former minister of finance, the only way to stop the EU’s complete disintegration is to further democratize it: On Feb. 9, the fiery economist established a pan-European movement called DiEM25, aimed at bringing greater democracy and transparency to the EU. Supporters include Wikileaks founder Julian Assange, musician Brian Eno, philosopher Slavoj Žižek and MIT theorist Noam Chomsky.
Varoufakis spoke to Quartz about his star-studded movement and how it hopes to fix the EU. Quartz: DiEM25 is not a political party. Check out these awesome wood phone cases from Carved. Apple is openly defying US security orders, but in China it takes a very different approach. After years of economic turmoil, a near-Grexit, a looming Brexit, and a refugee crisis that challenges the very principle of open borders, it’s safe to say that the European Union is struggling.
According to Yanis Varoufakis, Greece’s unforgettable former minister of finance, the only way to stop the EU’s complete disintegration is to further democratize it: On Feb. 9, the fiery economist established a pan-European movement called DiEM25, aimed at bringing greater democracy and transparency to the EU. Supporters include Wikileaks founder Julian Assange, musician Brian Eno, philosopher Slavoj Žižek and MIT theorist Noam Chomsky.
Yes, the NSA Worried About Whether Spying Would Backfire. There’s no denying that technology is playing a bigger role in politics than ever before.
Whether that’s a good or bad thing for the electoral process, though, is still subject to debate. Now, a new report released by Yahoo suggests that the way you perceive the Internet’s role in politics may have a lot to do with your race. The report, which is being released today in advance of Yahoo’s Digital Democracy conference in Des Moines, Iowa, shows a deep divide between how white voters and minority voters view the potential for tech to improve political inclusion. Report: Hillary May Have Had Second Server. Discrepancies regarding when emails were erased from Hillary Clinton's private server have raised questions of whether the former secretary of state had a device other than the one that was recently obtained by the FBI.
"There's pretty definite time stamps when you move information from one computer to another," Marcus Rogers, head of computer information technology at Purdue University, told The Washington Examiner on Saturday. "Somebody knows exactly when this happened because those time stamps are there. " Platte River Networks, the Denver-based company that managed Clinton's email network after she left the State Department in 2013, told the Examiner earlier this month that it had transferred the data from Clinton's original private server later that year.
K-12 Outreach. According to the Department of Labor1, over fifty percent of jobs created in the future will require a background in math, science and technology.
Added to that, looming baby boomer retirements are expected to severely deplete the (Science, Technology, Engineering, and Mathematics) STEM workforce over the next decade. As the U.S. now trails in the amount of science and engineering degrees offered internationally, there is no better time than now to improve the participation and performance of younger students in STEM. Equipping young students with the inspiration, initiative and curiosity to pursue STEM fields is a top priority. MIT is very active in advancing STEM literacy through a diverse portfolio of K-12 outreach programs (link is external).
Using an Object-oriented Framework to Construct Wide-area Group ... - Richard Andrew Golding, Darrell Don Earl Long. A Longitudinal Survey of Internet Host Reliability - Darrell Long, Andrew Muir, Richard Andrew Golding. Resilient Memory-resident Data Objects - Jehan-François Pâris, Darrell Long. Analysis of replication control protocols - Darrell Long, University of California, Santa Cruz. Computer Research Laboratory.
A weak-consistency architecture for distributed information services - Richard Golding, University of California, Santa Cruz. Computer Research Laboratory. Group membership in the epidemic style - Richard Golding, Kim Taylor, University of California, Santa Cruz. Computer Research Laboratory. Science & health. Hackers. Fighting BDS in the Name of Human Rights. There is a growing and widespread concern among Jews in Israel and outside, and among friends of Israel everywhere, at the increasing threat posed by the BDS movement.
Zen and the Art of the Internet - Table of Contents. Predicting The Future: Fantasy Or A Good Algorithm? After failing to predict the Arab Spring, intelligence officials are now exploring whether Big Data, the combing of billions of pieces of disparate electronic information, can help them identify hot spots before they explode.
The intelligence community has always been in the business of forecasting the future. The question is whether tapping into publicly available data — Twitter and news feeds and blogs among other things — can help them do that faster and more precisely. DBI-1.633 - Database independent interface for Perl. D 70, 123505 (2004) - DBI in the sky: Non-Gaussianity from inflation with a speed limit. DBI. DBI - Database independent interface for Perl The synopsis above only lists the major methods and parameters.
General. DBI Advanced Tutorial 2007. [ Mibbit ] Radiol. ATHENA, ARTEMIS, HEPHAESTUS: data analysis for X-ray absorption spectroscopy using IFEFFIT. Volume 12, Part 4 (July 2005)
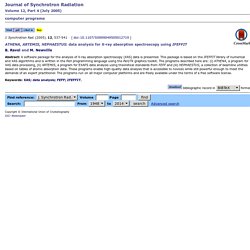
FireEye’s Kevin Mandia: Identifying Hackers Is Getting More Difficult. Hackers aren’t just getting more aggressive — take a look at what happened last winter to Sony — they’re also getting harder to track down.
The Third Phase of Big Data. Back in the pre-Internet era of the ’70s and ’80s, computer enthusiasts and researchers used “sneakernet” — loading information onto a portable storage device and walking it over, as a way to move large files. Mechanism for establishing the trust tree - Google Inc. 1. Field Aspects of the example implementations relate generally to data management, and more specifically, to managing access and display protocols for sensitive data. 2. Background Users often utilize “third party” applications and grant permission to sensitive user data (e.g., personal user information such as name, address, phone number, etc.) based on difficult to understand, or noisy permission negotiations.
In an example, the user utilizes an application to conduct an online interaction (e.g., blog comment, liking a social media post, posting a photo, etc.), which is tagged with user information. Consider the related art example of FIG. 1, wherein a user is running a third party application 101 within a social media website in a web browser 100. Patent US20140040626 - Anonymization and reattribution framework for offline identifiers - Google Patents. Aspects of the present application relate generally to the field of processing data associated with a user. More specifically, certain implementations of the present disclosure relate to anonymization and reattribution framework for offline identifiers. The expansion of unique identifiers (e.g., barcodes, quick response (QR) codes, radio frequency identification (RFID) tags, near field communication (NFC) proximity sensors, GPS units) into the offline space means users will be at risk of significant privacy harm if such identifiers are stolen and then traced back to the respective users.
As users have acquired more offline devices with identifiers (e.g., watches with NFC chips, clothing apparel with unique barcodes or QR codes, RFID tags on bicycles, etc.), they have lost the ability to manage offline analytics data related to usage of the offline device. Patent US20140040626 - Anonymization and reattribution framework for offline identifiers - Google Patents. Patent US20140258276 - Social annotations for enhanced search results - Google Patents.
The Internet provides access to a wide variety of resources, such as image files, audio files, video files, and web pages. A search system can identify resources in response to queries submitted by users and provide information about the resources in a manner that is useful to the users. The users then navigate through (e.g., click on) the search results to acquire information of interest to the users. Users of search systems are often searching for information regarding a specific entity. Evaluating the Impact of Science, Technology and Innovation Programs: a Methodological Toolkit. Tech News, Reviews & Analysis. This May Be Why You’re Seeing the Dress as White and Gold. The Internet officially broke on Thursday night thanks to a dress that had defied the classification of color. Is it white and gold or is it black and blue? “I’ve studied individual differences in color vision for 30 years, and this is one of the biggest individual differences I’ve ever seen.”
The Science of Why No One Agrees on the Color of This Dress.