

Mailinator(tm) Blog. Backup remoto de bases de datos MySQL con mysqldump. Las bases de datos guardan información fundamental para nuestro negocio o actividad, y un aspecto a tener muy en cuenta es realizar copias de seguridad o backups regulares tanto de los datos que contienen como de su estructura.

Las webs, como aplicaciones que son, no están exentas de necesitarlas, pues ya sea por ataques o por desgracias físicas de los servidores en las que están alojadas, no podemos permitirnos dejar a nuestros usuarios o visitantes sin servicio, así que es necesario contar con una buena política de copias de seguridad. Si tenemos una web, blog, servicio online, etc y utilizamos una base de datos MySQL podemos emplear diferentes mecanismos para realizar la copia de seguridad, por ejemplo entrar enphpMyAdmin, si disponemos de él, y hacerla manualmente. Mysqldump -h [nuestro.servidor.com_o_IP] -u [usuario] -p[password] [base_de_datos] > archivo_backup.sql Este comando nos creará el archivo archivo_backup.sql con el contenido de la base de datos que le hayamos indicado.
. #! Recover MySQL root Password. You can recover MySQL database server password with following five easy steps.
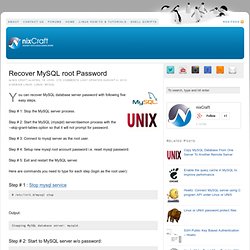
Step # 1: Stop the MySQL server process. Step # 2: Start the MySQL (mysqld) server/daemon process with the --skip-grant-tables option so that it will not prompt for password. Step # 3: Connect to mysql server as the root user. Step # 4: Setup new mysql root account password i.e. reset mysql password. Step # 5: Exit and restart the MySQL server. Here are commands you need to type for each step (login as the root user): A Recovering Physicist: How To Move A Mailman Mailing List Between Domains Or Servers. I have a VPS (virtual Private Server) running CentOS 5.4 and Plesk Web-hosting management software.

Under Plesk, Mailman is installed; this mailing-list management package is not necessarily present by default in Linux distributions. I host a few dozen domains with a number of Mailman mailing lists scattered across them. Recently I had occasion to move a mailing list from one domain to another on the same server. It was not immediately clear how to go about this, and Googling didn’t turn up much that was helpful. So I’m documenting the process here in case it proves useful to others. The technique, with suitable modifications, works as well to move a list from one Linux server to another. Caveat The file-system locations I discovered for components of the Mailman infrastructure may be dependent on Plesk. . # find / -name \*archives\* -print | grep 'private' | more Overview and tools To move a list, it must be deleted and recreated.
Top 8 Tools For Linux / Unix Memory Forensics Analysis. You can dump Linux or Unix server memory.

This is useful for forensics analysis, and testing your own system. This is often desirable to see: What code and what data actually resides in memory.You can search for specific pids memory.Search memory for string and other data such as passwords.Works as add-on tool for gdb and others.Search/replace/dump memory from running processes and core files.All kinds of deep hacking activities that simply saves your time and solve problems. LiME (Linux Memory Extractor) From the project home page: LiME (formerly DMD) is a Loadable Kernel Module (LKM), which allows the acquisition of volatile memory from Linux and Linux-based devices, such as those powered by Android. => Download LiME Draugr By using /dev/(k)mem or a memory dump, Draugr can be used to access easily in python to this memory, play (read, write, disassemble, search) with it … and can find system information (processes …) by different methods. => Download draugr Volatilitux Memfetch Memgrep Memdump.
Manual de OpenLDAP en Linux. Debian copy/paste Tutorials - Linux Tutorials - 5 Steps to Secure your SSH Server. SSH is the standard method for Admin’s to connect to Linux servers securely.

But the default install of SSH server way far from perfect and may allow attackers to hack your server. This guide shows you how to secure your SSH server in few steps 1. Use Strong SSH Passwords Try to make all your passwords more secure by following next rules: Try to use minimum of 8 charactersUse upper and lower case lettersAlso use numbers in your passwordspecial characters like #$&* You have also a password generator in Linux called pwgen. Apt-get install pwgen pwgen command will generate a list of passwords of 8 characters. 2. To disable root logins edit sshd_config file located in /etc/ssh/ directory. # Prevent root logins: PermitRootLogin no.
Windows.