

Exploit Exercises. Crack the Code Challenge - Hak5. About Do you have what it takes to compete in the Crack The Code Challenge?
Test your skills in our private lab network and bid for the title supreme leet hax0r. Winners will be featured on future episodes of Hak5! How to play Sign up for a free trial of GoToAssist using the coupon code “HAK5″Submit your 9-digit support session code using for form belowYou will be connected to a computer on the Hak5 Lab networkOnce connected you will be presented with a challenge in the fields of systems administration, penetration testing or reverse engineeringUse skills demonstrated on Hak5 and the tools provided, or feel free to use the GoToAssist Express upload function to bring your own tools.The official chat room for the event is irc.hak5.org #hak5 Sign Up. Finding Old Apps for Pen Testers in Training.
We’ve heard of this OldApps.com many times before but a recent tweet from @taosecurity mentioning it put this resource over the top that we had to write it up for those in pen testing, exploit creation, … or just testing overall.
You’re not going to find any licensed software but it’s a great place for grabbing that old copy of Firefox or Adobe Reader for you to test against. Here’s the description from OldApps.com themselves. While most web-sites provide downloads of current versions, OldApps.com caters to a different market of interest by providing older versions of the same useful programs. Often newer versions are more complicated to use and we understand that it is hard to find older, more user-friendly versions of popular software. Many software providers do not include older versions of their software on their sites, therefore, OldApps.com has found its market niche and provides a vital intermediary function for our users’ software needs. PNTSTR.com. PentesterLab.com.
Category:OWASP CTF Project. Main Welcome to the OWASP Capture The Flag (CTF) project!
What is the CTF The OWASP CTF project is a web base hacking challenge application with challenges categorized in web, network and ‘others’. You require creativity, resourcefulness and networking skills to solve the various challenges. (a copy of the Live CD can help as well) Open Source? First of all... sorry, but of course, we can not make the CTF and all challenges opensource. Ahead of the OWASP AppSec-NY in 2009, the idea came up to supply an OWASP CTF event. Can I help? Shure, we need people who can help in designing and building challenges. The CTF at your event Unfortunately, and I guess you understand, we can't share the current used CTF freely..
To get the CTF at your (OWASP) event, send an email to steven.van.der.baan 'at' owasp.org This category currently contains no pages or media. OWASP Hackademic Challenges Project. Main The OWASP Hackademic Challenges Project is an open source project that helps you test your knowledge on web application security.
You can use it to actually attack web applications in a realistic but also controlable and safe environment. Download the current version (v.0.1.1) from Google Code. Development version Github Latest changes implemented in the 'next' branch You can also challenge yourself using the live version hosted here: Live version in Greek language (includes additional challenges): The OWASP Hackademic Challenges have been now also integrated into the Hacking Lab. Overview The Hackademic Challenges implement realistic scenarios with known vulnerabilities in a safe, controllable environment. Currently, there are 10 web application security scenarios available. Target Group. Hackademic.
CTF365 | Hackables - IT Security. Hackery > CTF / Wargames : OWASP Mantra - Free and Open Source Browser based Security Framework. Capture the flag wrapup. Update: We've also posted downloadable Stripe CTF disk images, available by direct download or BitTorrent.
You're free to use the disk images to do your own cool things. The Stripe code on the disk images is licensed under a BSD license. Third party code included in the disk images is subject to its own license, which is included. We'd appreciate you letting folks know where you got the original code and we'd love to hear what cool things you're doing (but that's up to you). Janos Gyerik has also created a Live CD image of the Stripe CTF that makes it even easier to get started.
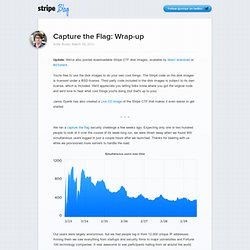
We ran a capture the flag security challenge a few weeks ago. Simultaneous users over time Our users were largely anonymous, but we had people log in from 12,000 unique IP addresses. Network, IT Penetration Testing, Ethical Hacking Training Courses. Holiday Challenge 2013 is now available. Editor's Note: One of my favorite Rankin and Bass Christmas specials is The Year without a Santa Claus. I simply love the songs of the weird and unforgettable Miser Brothers, and have frequently found myself humming their tunes during the holiday season.
I've always wanted to write a hacking challenge themed around them, and with my recent work on SANS NetWars CyberCity, my interest in the security of Industrial Control Systems, and the ability to collaborate with Tim Medin on a challenge, this seemed like the right time to roll it out. We'll award prizes to the best technical answer, most creative answer that is technically correct, and one to the winner of a random draw. So, regardless of how deep you get into the challenge, please do submit your answers to holidayhack@counterhack.com on or before January 6, 2013 to win! The Year Without a Santa... A Miser Brothers Weather Control System Challenge By Ed Skoudis & Tim Medin When Mrs. WarZone [brmlab] Goals of the Project hakc teh pla.net improve our háčking skills phun for members of our hackerspace and members of other hackerspaces, also for visitors of our space Wargames (team) “Capture the Flag (CTF) is a computer security wargame.
![WarZone [brmlab]](http://cdn.pearltrees.com/s/pic/th/warzone-brmlab-22877735)
Each team is given a machine (or small network) to defend on an isolated network. Teams are scored on both their success in defending their assigned machine and on their success in attacking other team's machines. Network setup Vulnerable servers References. Secball. Sat 24 Mar 2012 reverse, fun, gb, hidden Last year, a friend and I started the stupid idea of making a GameBoy crackme based on the Pokémon® universe for the students of our school, in the context of an extra security project.
Unfortunately, too few students were motivated to even give it a try. But since I personally believe that at least one person on this planet is willing to become the best Pokémon Trainer Ever, I'm posting it on the Internet for him/her.
Hack a Server. Exploit Exercises. Cyber Ranges Computer & Network Security Challenges. Roxor Arcade - Security Games | Hackables - IT Security. Wargames - OverTheWire | Hackables - IT Security. CySCA - Cyber Security Challenge Australia | Hackables - IT Secu. National Collegiate Cyber Defense Competition | Hackables - IT S. CSAW CyberSecurity Challenge | Hackables - IT Security. OS/VM/Etc | Hackables - IT Security. Crowdsourced Pentest | Hackables - IT Security.