

Examples. Cuckoo hashing. Cuckoo hashing example.
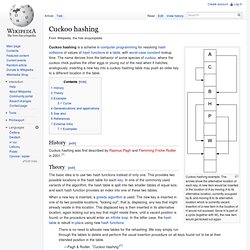
The arrows show the alternative location of each key. A new item would be inserted in the location of A by moving A to its alternative location, currently occupied by B, and moving B to its alternative location which is currently vacant. Insertion of a new item in the location of H would not succeed: Since H is part of a cycle (together with W), the new item would get kicked out again. Stop using unsafe keyed hashes, use HMAC « root labs rdist. The HMAC construction turns a cryptographic hash algorithm into a keyed hash.

It is commonly used for integrity protection when the sender and recipient share a secret key. It was developed to address various problems with arbitrary keyed hash constructions. So why are developers still rolling their own? One of the original papers on keyed hash constructions describes the motivations for developing a standard for HMAC. In 1995, there was no standardization and cryptographers only worked from hunches as to what constituted a secure keyed hash.
Locality-Sensitive Hashing for Finding Nearest Neighbors. CMPH - C Minimal Perfect Hashing Library.