

The Mystery of Duqu 2.0: a sophisticated cyberespionage actor returns. Duqu 2.0: Frequently Asked QuestionsDuqu 2.0 Technical Paper (PDF)Indicators of Compromise (IOC)Yara rulesPress release Earlier this year, during a security sweep, Kaspersky Lab detected a cyber-intrusion affecting several of our internal systems.
Following this finding, we launched a large scale investigation, which led to the discovery of a new malware platform from one of the most skilled, mysterious and powerful groups in the APT world – Duqu. The Duqu threat actor went dark in 2012 and was believed to have stopped working on this project – until now. Our technical analysis indicates the new round of attacks include an updated version of the infamous 2011 Duqu malware, sometimes referred to as the stepbrother of Stuxnet.
We named this new malware and its associated platform “Duqu 2.0”. Some of the new 2014-2015 Duqu infections are linked to the P5+1 events and venues related to the negotiations with Iran about a nuclear deal. MD5s Action loaders: Cores: C&C IPs. V Locker (variante de Cryptolocker) - La fin du cauchemar ? From the Labs: New developments in Microsoft Office malware. In September 2014, we wrote about a resurgence in VBA malware.

VBA stands for Visual Basic for Applications: it is a powerful and very widely-used programming tool that can be used right inside applications such as Microsoft Office. That makes it common, and indeed perfectly usual, in legitimate files. But, as we we wrote last time: Visual Basic code is easy to write, flexible and easy to refactor. Similar functionality can often be expressed in many different ways which gives malware authors more options for producing distinct, workable versions of their software than they have with exploits. In short, what is good for the gander is equally good for the goose. Indeed, over the past six months, malware that arrives as a VBA program inside an innocent-looking document has become an all-too-common occurrence in the threat landscape, and an essential weapon in spam campaigns. Backward compatibility Obviously, attackers who use VBA rely on their victims having some version of Office installed.
NYPD cop arrested for hacking into FBI, traffic databases. A New York City Police Department (NYPD) auxiliary deputy inspector was arrested on Wednesday morning for allegedly breaking into restricted law enforcement databases, including one maintained by the FBI.
In a press release, the FBI allege that Yehuda Katz, 45, assigned to the 70th Precinct in Brooklyn, was after the personal information of thousands of people who'd been in traffic accidents. He then allegedly posed as an attorney who could help the victims press legal charges. The criminal complaint claims that Katz snuck in to the Traffic Safety Office of the 70th Precinct and surreptitiously installed multiple electronic "devices" that let him remotely access restricted NYPD computers and law enforcement databases, including one maintained by the FBI, none of which he had permission to access. One of the devices Katz allegedly installed was a hidden camera that captured a live image of the office and was capable of live-streaming over the internet. and.
Comprendre Cryptolocker. Edité par CryptoLocker et ses dérivés comme CryptoWall, TorrentLocker, Synolocker, CTB-Locker sont des chevaux de Troie destinés à extorquer les gens.
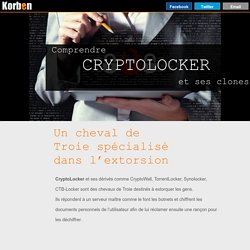
Ils répondent à un serveur maître comme le font les botnets et chiffrent les documents personnels de l’utilisateur afin de lui réclamer ensuite une rançon pour les déchiffrer. Dès que le chiffrement est terminé et que les fichiers sont devenus inaccessibles, Cryptolocker ou ses variantes affichent un message comme celui que vous pouvez voir ci-dessus, réclamant un versement (via carte prépayée ou Bitcoin) d’environ 500 $ pour fournir la clé de déchiffrement à la victime. Le premier malware qui infecte les drones. Ex-con Kevin Mitnick now selling zero-day exploits, starting at $100K.
Kevin Mitnick isn't known for being humble.
When Paul Ducklin reviewed the infamous convicted phone hacker's Ghost in the Wires a few years ago, he noted that the book contained nary a word of contrition (granted, many readers disagreed with him on the need for any): He doesn't apologise to the very many victims he abused, lied to and cheated; nor to those whose cellphone time he ripped off and whose identities he stole; nor to those outside his own circle whom he left in potentially serious trouble or whose lives he diminished by his self-obsessed criminality. In fact, he doesn't really acknowledge his victims at all, and he gave me the impression that he's still proud of his time as a liar and a cheat.
So it probably shouldn't surprise anybody that Mitnick, who post-prison reinvented himself as a skilled penetration tester, security consultant and social engineer, is now offering to sell zero-day exploits at the eye-popping opening price of $100,000 (£61,283). Google DDoS. Le blogueur Chr13 a découvert une technique permettant de lancer une attaque DDoS via Google Docs... c'est-à-dire en utilisant les serveurs de Google directement.
Il lui suffit de trouver un bon gros fichier à télécharger sur le site de la victime... Un PDF par exemple. Puis de l'appeler comme si on appelait une image, directement dans Google Spreadsheet (le tableur).