

How To Setup a Basic IP Tables Configuration on Centos 6. Intro This article will show how to create a simple firewall on a Centos VPS.
It will only open up ports that we want and close up other services. I will also show how to prevent simpler attacks, and how to let yourself back in to the VPS if you deny access to yourself by accident. The tutorial is not by any means exhaustive and only shows how to open up a few incoming ports: for apache, SSH and email and close all the others. We will not be blocking any outgoing traffic, and only create a few most common rules to block the usual scripts and bots that look for vulnerable VPS. HowTos/Network/IPTables. 1.
Introduction CentOS has an extremely powerful firewall built in, commonly referred to as iptables, but more accurately is iptables/netfilter. Iptables is the userspace module, the bit that you, the user, interact with at the command line to enter firewall rules into predefined tables. Netfilter is a kernel module, built into the kernel, that actually does the filtering. There are many GUI front ends for iptables that allow users to add or define rules based on a point and click user interface, but these often lack the flexibility of using the command line interface and limit the users understanding of what's really happening.
Before we can really get to grips with iptables, we need to have at least a basic understanding of the way it works. Chains These are 3 predefined chains in the filter table to which we can add rules for processing IP packets passing through those chains. INPUT - All packets destined for the host computer. Building a Professional Firewall with Linux and Iptables. My first position out of university was working as a firewall engineer for a large credit card processing company.

It’s where I learned the way of the packet and how to build a proper firewall ruleset. Iptables. Translation(s): English - Italiano- Español NOTE: iptables is being replaced by nftables starting with Debian Buster Iptables provides packet filtering, network address translation (NAT) and other packet mangling.
Linux Network IP Accounting. I need to know how much data are transmitted on my ppp0 network or eth0 Internet links?
How do I set IP accounting by address such as 123.1.2.3 and 123.1.2.4? How do I set IP accounting per Apache virtual domain? How do I set accounting by service port (http, smtp) and protocol (tcp, udp, icmp)? How do I record how much traffic each of the clients computer is using? You don't have to install anything special. Sample Setup. Linux Firewall Configuration and Setup - iptables. Iptables 1 Set Up a Simple Firewall. Gentoo tutorial: iptables - seting up iptables and propper logging. Iptables on Gentoo really no different than any other distribution.
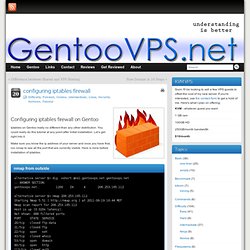
You could really do this tutorial at any point after initial installation. Let’s get right into it. Make sure you know the ip address of your server and once you have that, run nmap to see all the port that are currently visible. Here is mine before installation of iptables. Linux Firewall (iptables) Tutorial - PC Perspective Forums.
Iptables « Linux Systems and Network Administration. The Linux kernel, since version 2.0, has included the capabilities to act as a firewall.
In those days, the kernel module was called ipfwadm and was very simple. With the 2.2 kernel, the firewall module became called ipchains and had greater capabilities than its predecessor. Today, we have IPTables, the firewall module in the kernel since the 2.4 days. IPTables was built to take over ipchains, and includes improvements that now allow it to compete against some of the best commercial products available in the market. Iptables Howto — Fedora Unity Project. Iptables. Network/IPTables. Ch14 : Linux Firewalls Using iptables.
Network security is a primary consideration in any decision to host a website as the threats are becoming more widespread and persistent every day.
One means of providing additional protection is to invest in a firewall. Though prices are always falling, in some cases you may be able to create a comparable unit using the Linux iptables package on an existing server for little or no additional expenditure. Neat tricks with iptables. The past few months have seen me digging deep into the world of TCP/IP and firewalls.
It has been a fascinating journey into packet queueing and TCP headers, three-way handshakes and ICMP broadcasts. The result of this research has been the ongoing creation of a firewall to protect my laptop against open networks, and my Internet server from port scanning and DoS attacks. I’m pretty certain I haven’t even scratched the surface yet, but I have found some settings to protect against the most common attacks. Below I’ll summarize the major pieces of my new firewall, and the logic behind it. Basic Iptables - Debian/RedHat. Summary You can find an easier to read version here: 5dollarwhitebox.org Alot of people are freaked out by IPTables and find it hard to understand.
However, once you get the grasp of it the basics are easy. Simple firewall for Ubuntu using iptables. Linux's built-in firewall iptables is very useful, but pretty hard to configure. I used to use lokkit, but this caused problems when moving between different networks. I was also having problems with the network configuration tools in Ubuntu, which work but aren't automatic enough for me. And I wanted to be able to switch the firewall and the network configuration simultaneously. In the end, I bit the bullet and worked out how to write a simple iptables script. Here it is: #! I have network interfaces on eth0 and eth1, so this script has rules which cover both; if your interfaces have different names, you will need to edit the rules to cover that. I put this script in /opt/scripts/iptables.script and made it executable. NAT with Linux and iptables - Tutorial (Introduction) Introduction Network Address Translation generally involves "re-writing the source and/or destination addresses of IP packets as they pass through a router or firewall" (from This tutorial should explain what Network Address Translation is about, what to use it for and how to configure it under Linux (or more generally Unix-derivates).
This introduction does not claim to be complete or covering all details, its main purpose is to provide the reader a feeling for what is possible and meaningful in modern computer networks and what is not. First of all the structure of an IP-packet will be considered. After a short overview of the possibilities of the (Linux-)kernel I will jump right into the main area of application of NAT, namely the connection of a private subnet to the internet using a router (in our case a linux machine with iptables). Linux: 20 Iptables Examples For New SysAdmins.
Linux comes with a host based firewall called Netfilter. According to the official project site: netfilter is a set of hooks inside the Linux kernel that allows kernel modules to register callback functions with the network stack. A registered callback function is then called back for every packet that traverses the respective hook within the network stack.
Iptables Firewall - Wiki. From Wiki. Stop brute force attacks with these iptables examples. First let's define with the help of Wikipedia what a dictionary attack is: Linux IPTables: Incoming and Outgoing Rule Examples (SSH and HTTP)