

Think that printer in the corner isn’t a threat? Think again.
The Noise Protocol Framework. Maltego Blog. Black box attack, hacking an ATM with Raspberry PiSecurity Affairs. Cybercriminals can hack ATM systems and force the to dispense the cash by sending command through a smartphone, in this attack scenario the mobile devices are used only to send commands to the ATM remotely once the attacker has physically connected it to the machine.
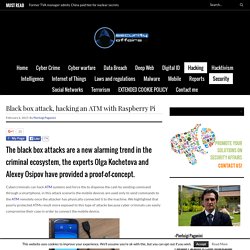
We highlighted that poorly protected ATMs result more exposed to this type of attacks because cyber criminals can easily compromise their case in order to connect the mobile device. Google Translate. Google Translate. Google Translate. Google Translate. Malware Taps Windows' 'God Mode' - Slashdot. Reader wiredmikey writes: Researchers at McAfee have discovered a piece of malware dubbed "Dynamer" that is taking advantage of a Windows Easter Egg -- or a power user feature, as many see it -- called "God Mode" to gain persistency (warning: annoying popup ads) on an infected machine.
God Mode, as many of you know, is a handy tool for administrators as it is essentially a shortcut to accessing the operating system's various control settings. Dynamer malware is abusing the function by installing itself into a folder inside of the %AppData% directory and creating a registry run key that persists across reboots. ITIL. Keystroke logging. A keylogger example of a screencapture, which holds potentially confidential and private information.
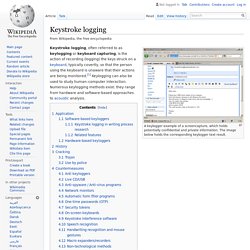
The image below holds the corresponding keylogger text result. Application[edit] Software-based keyloggers[edit] PrivateCore. PrivateCore is a venture-backed startup located in Palo Alto, California that develops software to secure server data through server attestation and memory encryption.
The company’s attestation and memory encryption technology fills a gap that exists between “data in motion” encryption (TLS, email encryption) and “data at rest” encryption (disk encryption, tape encryption) by protecting “data in use” (random access memory). PrivateCore memory encryption technology protects against threats to servers such as cold boot attacks, hardware advanced persistent threats, rootkits/bootkits, computer hardware supply chain attacks, and physical threats to servers from insiders. BitLocker. History[edit] BitLocker originated as a part of Microsoft's Next-Generation Secure Computing Base architecture in 2004 as a feature tentatively codenamed "Cornerstone" and was designed to protect information on devices, particularly in the event that a device was lost or stolen; another feature, titled "Code Integrity Rooting," was designed to validate the integrity of Microsoft Windows boot and system files.[3] When used in conjunction with a compatible Trusted Platform Module (TPM), BitLocker can validate the integrity of boot and system files before decrypting a protected volume; an unsuccessful validation will prohibit access to a protected system.[5][9] BitLocker was briefly called Secure Startup prior to Windows Vista being released to manufacturing.[5][9] Availability[edit] BitLocker is available on the Ultimate and Enterprise editions of Windows Vista and Windows 7, the Pro and Enterprise editions of Windows 8 and later,[1][2] and Windows Server 2008 and later.
Operation[edit] Trusted Platform Module. Components of a Trusted Platform Module TCG continues to revise the TPM specification.
It published revision 116 of the version 1.2 of TPM specification on March 3, 2011,[2] while the draft revision 1.07 of the version 2.0 of TPM specification was published for public review on March 13, 2014 as a library specification that provides updates to the previously published main TPM specifications. Trusted Platform Module Library Specification Revision 01.16 was released in October 2014 as the latest TPM 2.0 release.[3] Overview[edit] Trusted Platform Module offers facilities for the secure generation of cryptographic keys, and limitation of their use, in addition to a random number generator.[4][5] It also includes capabilities such as remote attestation and sealed storage, as follows: Generally, pushing the security down to the hardware level in conjunction with software provides more protection than a software-only solution.
Uses[edit] Platform integrity[edit] Triada Trojan the most sophisticated mobile malware seen to dateSecurity Affairs. Malware researchers at Kaspersky Lab have discovered a new strain of malware, dubbed Triada (Backdoor.AndroidOS.Triada), targeting Android devices, which they consider the most advanced mobile threat seen to date.
The range of techniques used by the threat to compromise mobile devices is not implemented in any other known mobile malware. Triada was designed with the specific intent to implement financial frauds, typically hijacking the financial SMS transactions. PoS malware detection volume grew 66% in Q3; SMBs most targeted. Most software already has a “golden key” backdoor—it’s called auto update. Leif Ryge is an artist, hacker, and journalist living in Berlin.
He used to tweet as @wiretapped but is on hiatus until Twitter stops suspending Tor users' accounts. In 2014 when The Washington Post Editorial Board wrote "with all their wizardry, perhaps Apple and Google could invent a kind of secure golden key they would retain and use only when a court has approved a search warrant," the Internet ridiculed them. Many people painstakingly explained that even if there were somehow wide agreement about who would be the "right" people and governments to hold such an all-powerful capability, it would ultimately be impossible to ensure that such power wouldn't fall in to the "wrong" hands.
IT Network and Sysadmins, using your default domain credentials as Domain Admins - Best Practices. Hello all IT pros, As a general rule of IT best practices and proper security - one does not generally use their own default domain account (domain\username) as part of the Domain Admins group for obvious safety and security reasons.
PCI DSS Version 3.2: What You Need to Know. In December of last year, the PCI Security Standards Council announced an extension of the deadline for the Secure Sockets Layer (SSL)/early Transport Layer Security (TLS) migration.

Businesses now have until June 2018 to transition to more secure protocols, giving them a bit more breathing room. In the same December bulletin, the PCI Council also announced the future release of PCI DSS version 3.2, slated for release in 2016. Now that the new year is well underway, the Council has released an update on what to expect and when. Here are the highlights. The Release of PCI DSS 3.2 is Coming Soon PCI Security Standards Council Chief Technology Officer Troy Leach says the new version is coming in the first half of 2016, most likely in March or April. Tripwire Enterprise: Advanced Threat Protection. Real-time Change Intelligence Get real-time threat detection and notification at the speed of change. Tripwire® Enterprise delivers change audit and threat detection with high precision, business context and insight for what to do about it. System Hardening and Compliance Enforcement Tripwire Policy Manager delivers proactive configuration hardening based on compliance requirements, reduces audit preparation time and cost, and provides audit-ready reporting with evidence of compliance, remediation and exception management.
Security Automation and Remediation Configuration errors need corrective measures. Tripwire Enterprise Product Brief Additional Resources Tripwire Enterprise Self-Guided Demo Watch Now. SANS Institute - CIS Critical Security Controls. The CIS Critical Security Controls for Effective Cyber Defense The CIS Critical Security Controls are a recommended set of actions for cyber defense that provide specific and actionable ways to stop today's most pervasive and dangerous attacks. A principal benefit of the Controls is that they prioritize and focus a smaller number of actions with high pay-off results.
The Controls are effective because they are derived from the most common attack patterns highlighted in the leading threat reports and vetted across a very broad community of government and industry practitioners. They were created by the people who know how attacks work - NSA Red and Blue teams, the US Department of Energy nuclear energy labs, law enforcement organizations and some of the nation's top forensics and incident response organizations - to answer the question, "what do we need to do to stop known attacks. " POS Breaches - OpenDNS Security Labs.